Managing IAM in one cloud environment is already a complex job. Add AWS, Azure, and Google Cloud to the mix, and it can feel like you’re managing three different operating systems while blindfolded. Each platform has its own logic, permissions model, tooling, and quirks, and making them work together securely is no small feat.
That’s why automation matters. Without it, you’re stuck duplicating work, copying configs, and hoping no one misses a role update during an incident.
In this deep dive, we’ll look at how to automate IAM across multi-cloud environments. You’ll get practical steps, sample tools, and real-world techniques to reduce risk and keep access consistent - without going insane.
1. Why Automate IAM in Multi-cloud?
Why not just manage IAM manually, cloud by cloud? Because the complexity stacks fast. A few environments, a handful of users, and suddenly you’re maintaining three sets of policies, with no guarantees they match.
Automation solves four core problems:
- Consistency: Everyone gets the same roles across environments, no matter the provider.
- Scalability: Onboarding a new team or application doesn’t require logging into three different consoles.
- Error Reduction: No more forgetting to remove access or misconfiguring a role in just one cloud.
- Speed: Roll out updates globally from a single source of truth.
In short: automation makes IAM predictable - and that’s what security needs.
2. Understand the IAM Landscape (Before You Automate Anything)
Before you can automate, you need to know what you’re automating.
Here’s how IAM works across the Big Three:
- AWS IAM uses policies attached to users, roles, and groups.
Think: JSON-based policies + federated access + STS tokens. - Azure AD is built on role assignments.
It includes tools like PIM (Privileged Identity Management) for just-in-time access. - GCP IAM relies on bindings that connect roles to members (users, service accounts, etc.)
scoped to resources.
The terminology’s different, but the goal is the same: restrict access to just what’s needed. Your job is to unify this using tools that abstract away those differences.
3. Step-by-Step Guide to Automating IAM
Step 1: Define Standard IAM Roles and Policies
Start by outlining what access looks like across your org.
- What do developers need across clouds?
- What does read-only access mean in each platform?
- Are there platform-specific roles (e.g., BigQuery admin) that don’t map directly?
Define these in Terraform, Pulumi, or another infrastructure-as-code tool. That way, your definitions live in version control and can be reviewed and deployed repeatably.
Step 2: Centralise Management with a Control Plane
Managing IAM in three separate portals won’t scale. Use tools like:
- AWS Organisations
- Azure Blueprints
- GCP Organisation Policies
Or, if you want vendor-agnostic control:
- Spacelift, Terragrunt, or Crossplane
These let you define IAM once, then deploy across environments.

Step 3: Automate Role Creation and Assignment
Use your IaC tool to create and assign roles consistently.
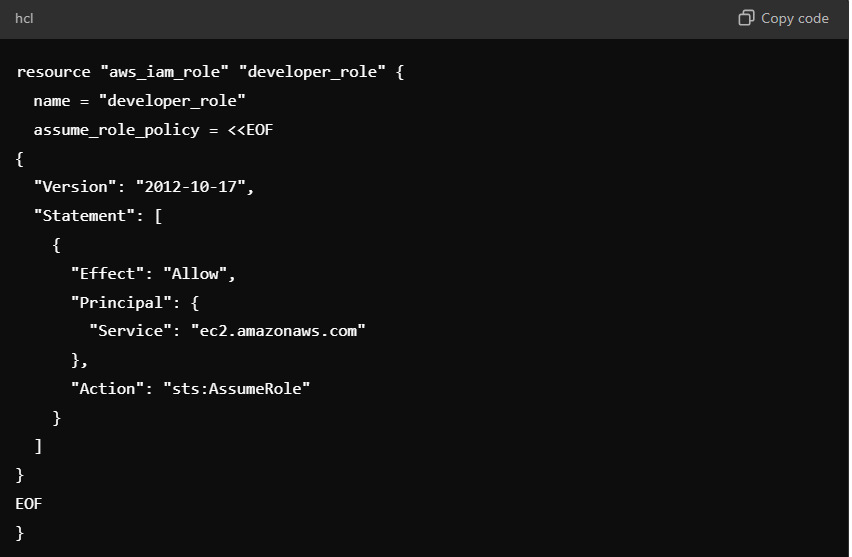
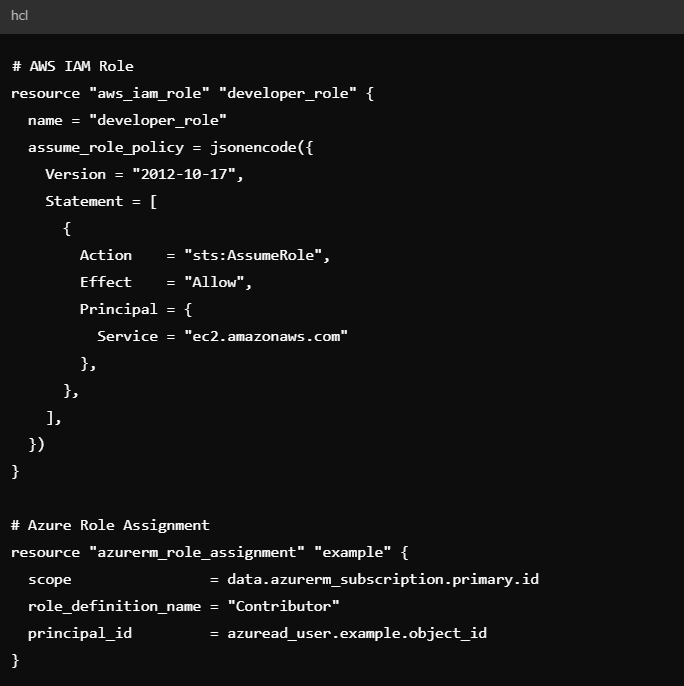
For example, in Terraform:
- Define an aws_iam_role for developers
- Mirror that with an azurerm_role_assignment
- Repeat for GCP’s google_project_iam_member
Now your team gets the right access, wherever they’re working.

Step 4: Automate Auditing and Reporting
Audits don’t scale manually. Use tools like:
- AWS Config
- Azure Policy
- GCP Policy Analyzer
- Cloud Custodian
Set up automated scans to:
- Flag overly broad access
- Alert on policy drift
- Generate compliance reports

Step 5: Automate IAM Policy Updates with GitOps
Finally, treat IAM like code.
- Store policies in GitHub
- Use ArgoCD or Flux to deploy changes to each cloud
- Add CI tests to validate configs before they go live
Now you’ve got versioned, auditable, and automatically enforced IAM.

4. What Can Go Wrong (and How to Fix It)
Challenge 1: Policy Mismatches
Not all clouds treat access the same. “Read-only” in Azure isn’t identical to GCP.
Fix: Build cloud-specific modules in Terraform to abstract the differences.
Challenge 2: Identity Federation Confusion
Multiple clouds + one SSO provider = confusion.
Fix: Standardise on a central IdP (e.g., Azure AD + SAML/OIDC) and map roles clearly across clouds.

Challenge 3: Automation Mistakes at Scale
One bad policy deployed everywhere? Yikes.
Fix: Always test in staging. Apply least privilege. Use CI tests for policy review.
5. Real-World Example: IAM Automation Across 3 Clouds
Company X runs:
- Core infra on AWS
- EU operations on Azure
- Data pipelines on GCP
They use Terraform to define shared roles (e.g., dev, admin, auditor)
and apply these via Spacelift to all three platforms.
- IAM policies live in GitHub
- ArgoCD pushes changes via pipelines
- Cloud Custodian runs weekly audits
Result: faster onboarding, better audit trails, fewer misconfigs.
Final Thoughts
Automating IAM across multi-cloud isn’t easy - but it’s doable, and necessary.
Use infrastructure as code to define access. Centralise where you can. Automate audits. And above all, treat IAM like software - versioned, tested, repeatable.
Get that right, and multi-cloud won’t feel so chaotic anymore. It’ll just be another part of your stack you’ve got under control.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand




