Building a Customised CloudTrail for Enhanced Security in AWS Environments

In today's fast-moving, cloud-driven world, knowing what’s happening inside your AWS environment is more than just a good idea - it’s crucial. That’s where AWS CloudTrail comes in. Think of it as your security camera, recording every API call that happens within your cloud infrastructure. It’s like having an audit trail of who did what, when, and where.
While AWS provides a strong default setup with CloudTrail, it may not give you the depth or flexibility needed for complex environments or strict compliance mandates. The good news? You can customise it to go deeper, track across regions, and plug into real-time monitoring tools like CloudWatch and SIEMs.
Let’s explore how to build a smarter, customised CloudTrail setup that works harder for you.
Understanding AWS CloudTrail: The Basics
AWS CloudTrail logs every API call made within your AWS account. It’s your audit log for tracking user activity, resource changes, and compliance.
CloudTrail captures:
- Who made the request
- When the request occurred
- What service and action was invoked
- Where the request came from (IP, region)
By default, CloudTrail logs management events like creating EC2 instances or modifying IAM roles.
For deeper visibility, you can enable data events (e.g., object-level S3 access) or anomalous behavior
tracking with CloudTrail Insights.
Benefits of Customisation
- Capture detailed reads/writes at the object level
- Monitor activity across multiple regions
- Lock down access to logs
- Set real-time alerts for suspicious behavior
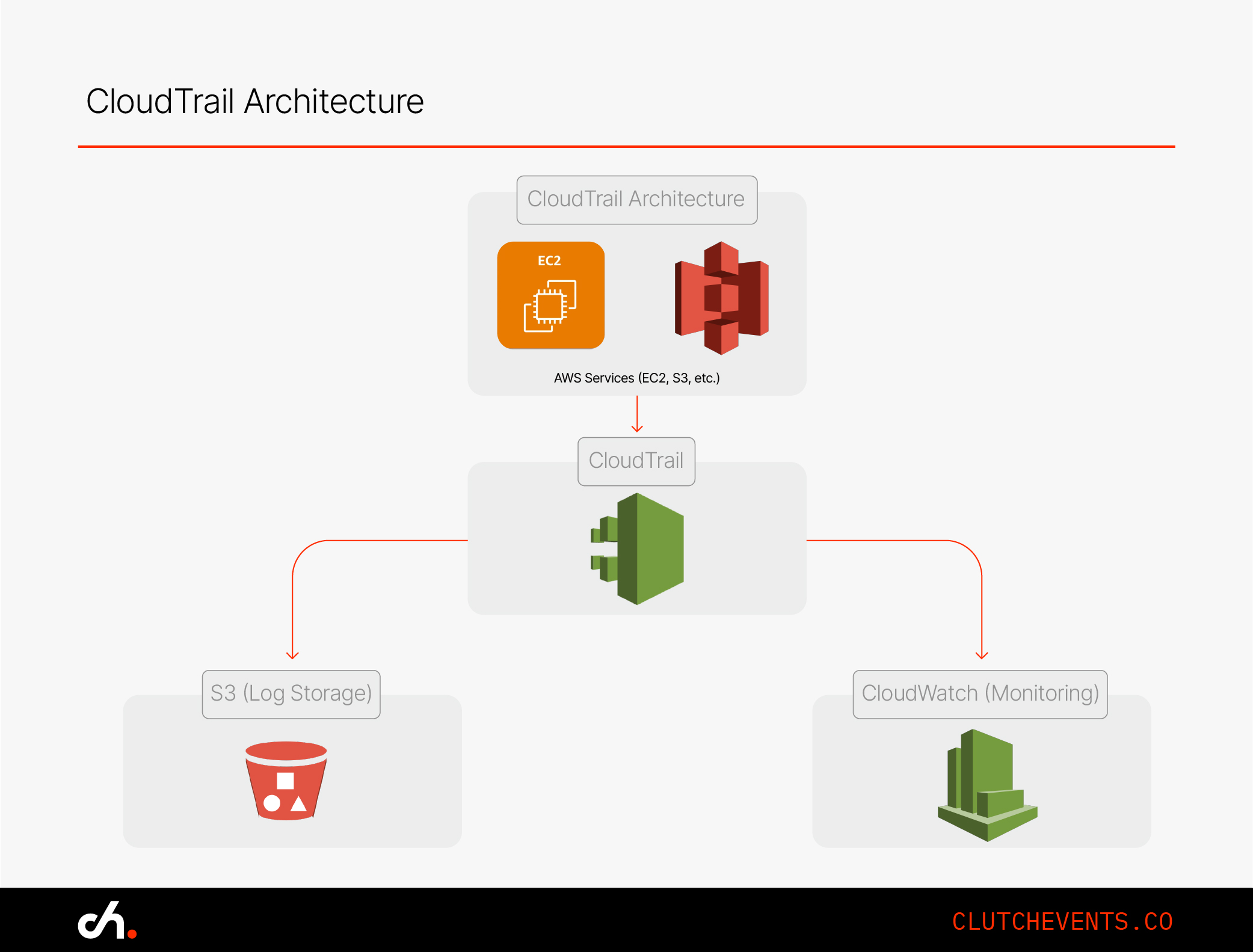
Why Customise CloudTrail?
Default settings are broad but shallow. If you need:
- Granular insights (e.g., who’s accessing S3 files)
- Cross-region visibility
- Automated detection and response
- Compliance-grade audit trails
...then it’s time to level up.
Step 1: Set Up an S3 Bucket for Logs
Your logs need a secure home.
Steps:
- Create a dedicated S3 bucket (e.g., cloudtrail-logs-org123)
- Enable versioning and encryption (KMS recommended)
- Apply least privilege IAM policies
Use customer-managed KMS keys with rotation policies for enhanced control.
Step 2: Create a New CloudTrail
Steps:
- Go to the AWS CloudTrail console → "Create Trail"
- Name it (e.g., OrgWide-Security-Trail)
- Point logs to your S3 bucket
- Enable log file validation for integrity checking
Step 3: Customise Event Types
Types:
- Management Events: High-level changes (e.g., EC2 launch, IAM role updates)
- Data Events: Detailed access logs (e.g., S3 file reads, Lambda executions)
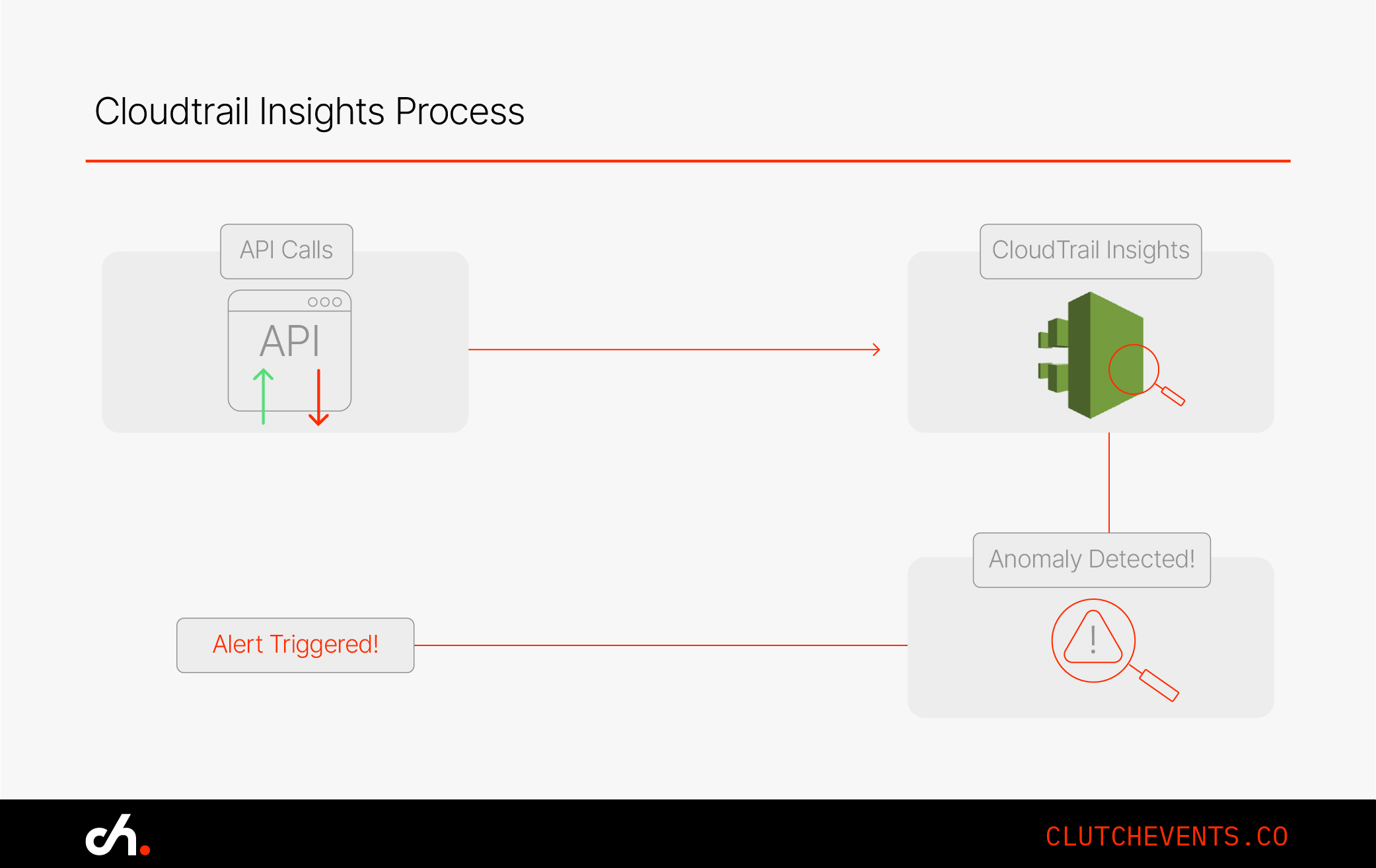
- CloudTrail Insights: Detects spikes or anomalies in API usage
Enable data events for sensitive data (PCI, PII) but be aware of cost implications.
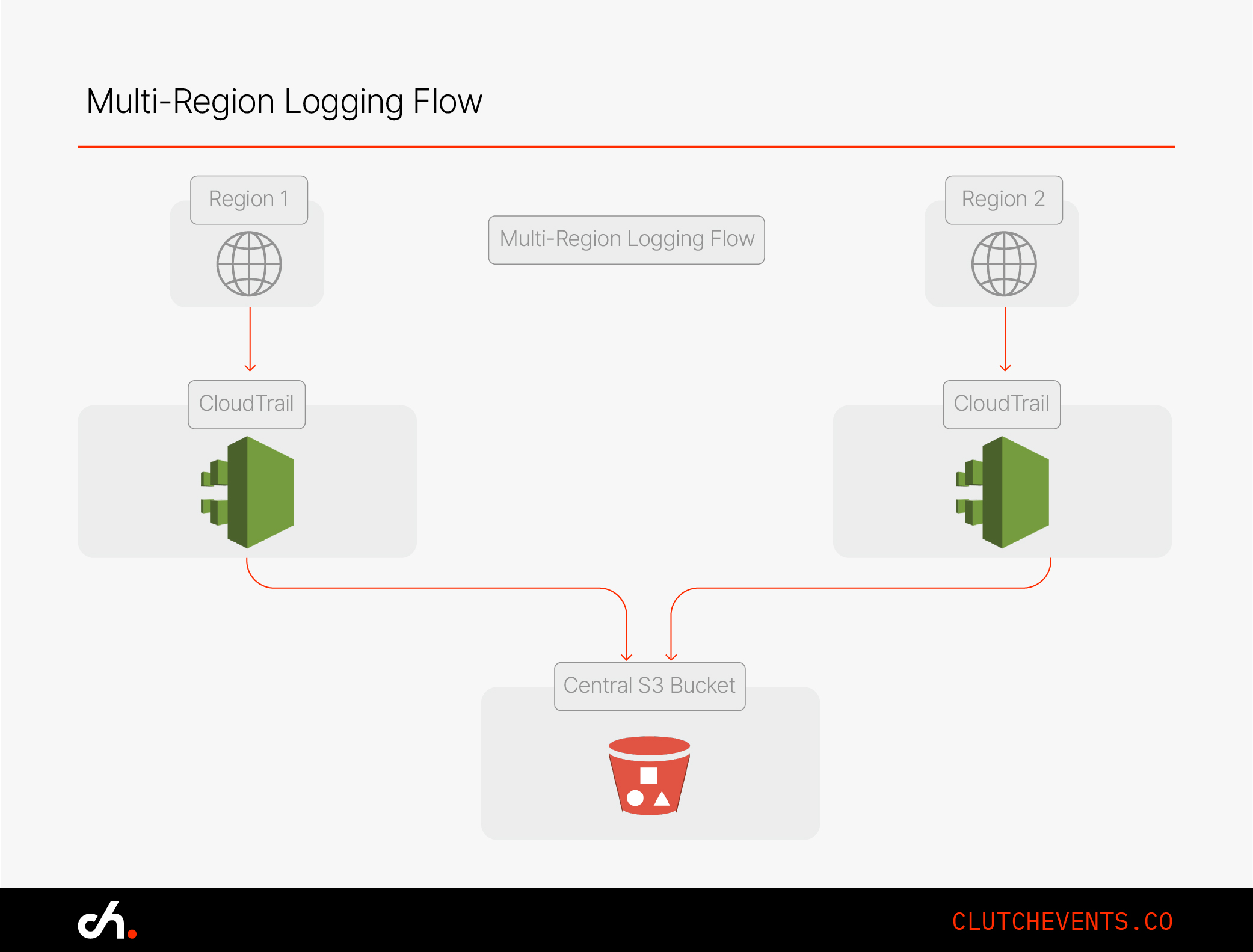
Step 4: Enable Multi-Region Logging
If you're operating in more than one AWS region, enable global logging for unified visibility.
Steps:
- While creating the trail, check "multi-region trail"
- For multi-account setups, consolidate logs into one bucket using AWS Organizations
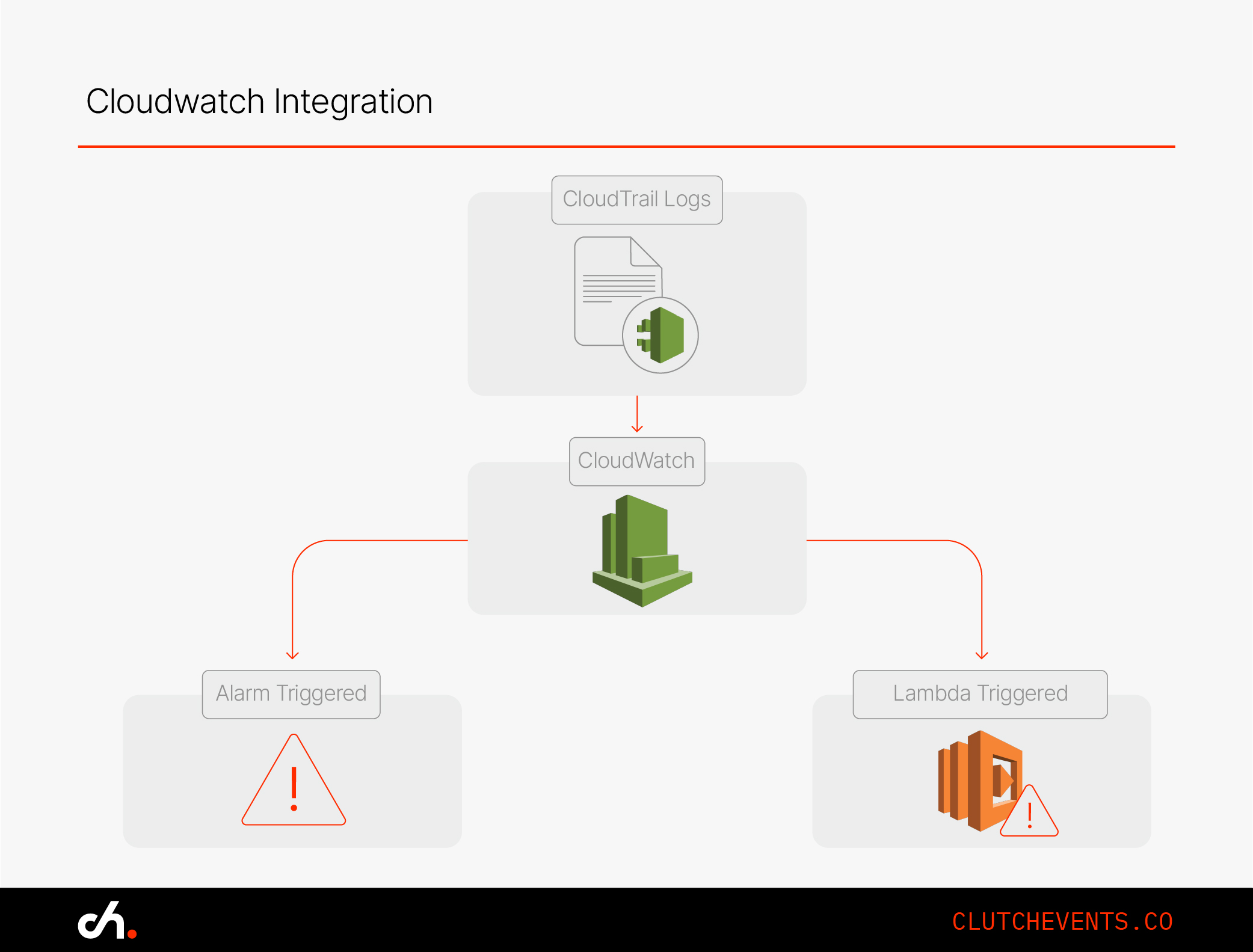
Step 5: Integrate with CloudWatch for Real-Time Alerts
CloudWatch + CloudTrail = proactive detection + automation.
Steps:
- Send CloudTrail logs to a CloudWatch Log Group
- Create alarms for key events (e.g., unauthorized IAM access)
- Trigger automated actions via SNS or Lambda
- For complex workflows, use EventBridge
Best Practices for CloudTrail Security
- Enable log file validation
- Use MFA and encrypted access to logs
- Use customer-managed KMS keys with key rotation
- Audit access with S3 Access Logs or CloudTrail Data Events
- Set S3 lifecycle policies for retention compliance
Advanced Use Cases
Automated Incident Response:
- Trigger Lambda on unauthorized changes → rollback policy + alert
- Integrate with AWS Config for compliance enforcement
Insider Threat Detection:
- Use CloudTrail Insights to detect unusual access patterns
Compliance Audits:
- Custom event logging makes passing audits easier
- Generate compliance artifacts with AWS Artifact
Conclusion
A customised CloudTrail setup transforms your AWS logging from passive to proactive. You gain visibility across regions, detect threats in real time, and meet compliance requirements with ease.
Use this guide to take your CloudTrail from basic to bulletproof and give your team the observability and control they need to protect what matters.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand



