The Cloud SOC Rebuild: Why Traditional Detection Engineering Doesn’t Scale

Most SOCs were designed for static infrastructure and centralised data. But today’s cloud environments are fast-moving, distributed, and built on constantly changing services. That’s why traditional detection engineering is breaking down and many teams are feeling it.
This briefing breaks down why the old approach no longer works, and how forward-thinking teams are redesigning detection pipelines, alert workflows, and feedback loops for modern cloud operations.
Why Traditional Detection Engineering Fails in the Cloud
1. Cloud Environments Change Daily
Rules tied to fixed IPs or static assets collapse in modern systems. Serverless functions appear and disappear. Containers redeploy frequently. Identities, not infrastructure, are now the true perimeter.
2. Data Lives Everywhere
Security signals come from multiple clouds, SaaS tools, and short-lived workloads. Legacy systems expect one SIEM or data lake. Cloud-native teams need to quickly ingest, correlate, and act on signals from many places.
3. Manual Rules Don’t Scale
In traditional SOCs, analysts write detection rules by hand. That approach falls apart in cloud setups where one misconfigured service can generate thousands of alerts or none at all.
4. Most Alerts Lack Context
Legacy detections often fire without understanding user intent or system state. In the cloud, the same action could be safe or suspicious…context is everything. Without it, teams drown in noise or miss real threats.
What the New Cloud SOC Looks Like
1. Identity-First Detection
Modern detection focuses on who did what:
- Which user or service account acted?
- What roles or permissions were used?
- Is this normal based on past activity?
2. Log-Centred, API-Aware Pipelines
Packet inspection won’t cut it. Cloud SOCs rely on logs (CloudTrail, Audit Logs, API telemetry) to understand behaviour over time:
- Parse and enrich logs automatically
- Correlate actions across cloud providers
- Detect patterns, not just isolated events
3. Alerts Prioritised by Blast Radius
Some alerts matter more than others. Leading teams ask:
- Could this identity change production?
- Is this step part of privilege escalation?
- Is high-value infrastructure involved (like KMS or IAM)?

4. Detection Is a Team Sport
Security and engineering teams now co-develop rules. Feedback is fast. Infrastructure tags and IaC metadata provide critical context. No more writing rules in isolation.
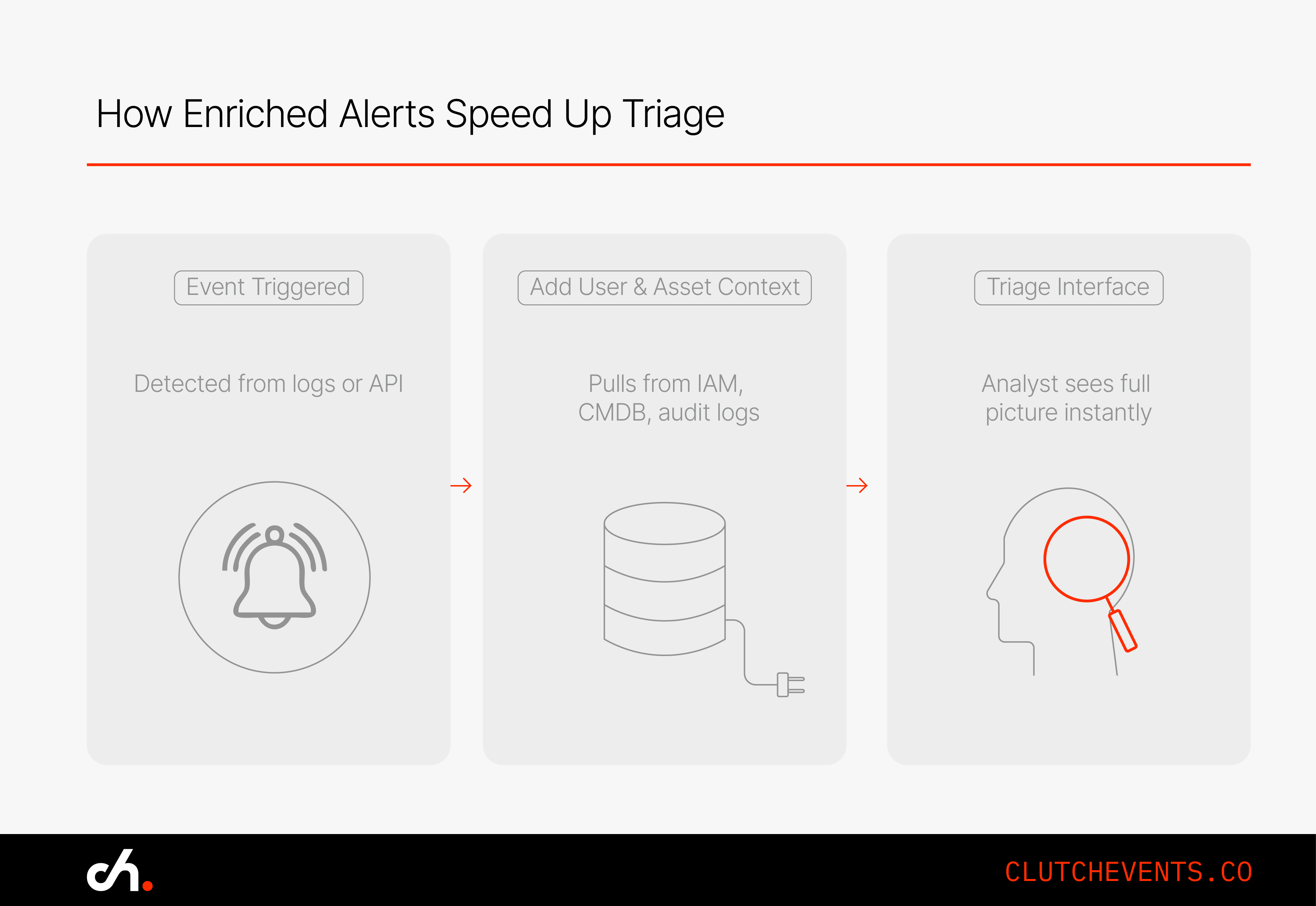
5. Triage Is Automated and Enriched
Every alert should come with
- Who did it and what they touched
- Recent related activity
- Suggested next steps
This way, humans spend time analysing, not digging for details.

Practical Steps to Rebuild Your Cloud SOC
1. Start With an Inventory of Logs
- What logs do you collect? What’s missing?
- Prioritise those that show access, privilege, and changes
2. Make Detection Identity-Centric
- Move away from IPs and devices
- Focus on what principals are doing and whether it’s expected
3. Use Native Tools to Ingest and Route Logs
- AWS: Kinesis Firehose, Lambda, OpenSearch
- GCP: Pub/Sub, Dataflow, BigQuery
- Azure: Event Hub, Log Analytics
4. Tune Alerts by Environment and Impact
- Treat dev and prod differently
- Prioritise by asset value and potential damage
5. Work With Cloud Engineers Early
- Involve DevOps and platform teams in shaping detection
- Use project labels, tags, and metadata to tag events automatically
6. Build Enrichment from the Start
- Link to asset inventories
- Enrich with user metadata (IAM, Okta, Azure AD)
- Add config data from your CMDB or Terraform state
Conclusion
The old SOC model wasn’t built for the cloud. It’s rigid, noisy, and slow to adapt.
The modern approach is identity-first, log-native, and context-rich. It involves platform teams and prioritises the alerts that matter.
If you want your SOC to keep pace with cloud infrastructure, rebuilding isn’t optional, it’s essential. It’s not a side project. It’s the core of your security future.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand


