Enforcing Fine-Grained Access Controls Across Hybrid Clouds: A Technical Deep Dive

Introduction
With the adoption of hybrid cloud infrastructures, combinations of public cloud services, private cloud environments, and on-premises resources, the need for precise, adaptable access control mechanisms has grown. Managing access within these distributed environments introduces complexities that traditional role-based access control (RBAC) models often can’t address on their own.
To ensure data security, meet compliance requirements, and prevent unauthorised access, fine-grained access control is becoming an essential security layer for hybrid cloud infrastructures.
Fine-grained access control allows organisations to enforce policies that define access based on attributes like user identity, device status, location, and other factors that provide context.
This article explores the unique challenges of enforcing fine-grained access in hybrid clouds, outlines key strategies, and provides best practices for securing these multi-environment assets.
Why Fine-Grained Access Control Matters in Hybrid Clouds
In hybrid cloud environments, fine-grained access control goes beyond broad, role-based permissions by enforcing policies with a level of specificity that addresses the more complex access demands. Hybrid clouds require policies that adapt to multiple environments while securing sensitive data and allowing users the access they need to do their jobs effectively.
Key Benefits of Fine-Grained Access in Hybrid Clouds:
- Enhanced Security: By tailoring access based on specific criteria, organisations can greatly reduce unauthorised access and potential breaches.
- Regulatory Compliance: Granular access controls help meet compliance requirements, ensuring that sensitive data is accessible only to those with the right permissions.
- Reduced Attack Surface: By limiting access to the minimum necessary for each user or system, fine-grained controls reduce potential exposure to threats.
- Improved Operational Efficiency: Access is granted based on user needs, simplifying the management of permissions across different environments and enabling faster responses to changing access requirements.
Think of it this way: Fine-grained access control is like establishing custom levels of clearance for each person, rather than offering all-or-nothing access. When sensitive data and applications are scattered across various environments, these detailed permissions help ensure that only authorised individuals can access specific resources, tailored to their needs and conditions.
Challenges of Enforcing Fine-Grained Access Control in Hybrid Clouds
Hybrid clouds present unique security challenges due to their distributed nature and the variety of platforms involved, each with its own policies and systems.
1. Lack of Centralised Management
Hybrid cloud setups distribute resources across multiple environments, often making centralised access policy management a challenge. This can result in security gaps and inconsistent enforcement.
2. Diverse Identity and Access Management (IAM) Standards
Cloud providers like AWS, Azure, and Google Cloud each have distinct IAM frameworks, making seamless integration difficult. Hybrid clouds often require private cloud or on-premises IAM frameworks to work with these public cloud standards.
3. Dynamic and Distributed Nature of Hybrid Clouds
Hybrid environments are inherently dynamic, with resources scaling up or down and users accessing applications from various locations. Enforcing access based on real-time attributes like device posture or location is complex in such environments.
4. Compliance with Multiple Regulatory Standards
Hybrid environments often require compliance with different regulatory standards (GDPR, HIPAA, CCPA). Fine-grained access control must align with these standards across diverse platforms within the hybrid setup.
Real-World Tip: Choose an IAM solution that supports hybrid environments and has centralised policy management capabilities, allowing for consistent access control across environments and easier management of compliance requirements.
Key Takeaway: Hybrid clouds introduce complexity that demands adaptive, unified access control solutions for secure and compliant access across all resources.
Key Strategies for Enforcing Fine-Grained Access Controls
Enforcing fine-grained access control across hybrid clouds requires a multi-layered approach. Here’s a breakdown of primary strategies for effective, granular access management:
1. Attribute-Based Access Control (ABAC)
Attribute-Based Access Control (ABAC) determines access based on attributes such as user identity, role, device health, access time, and location. This approach is more flexible than RBAC, as it can dynamically adjust based on real-time attributes.
- Think of ABAC as giving each access request a “quick background check” to confirm it fits criteria tailored to the task, the person’s role, and current conditions.
- Example: In healthcare, ABAC might allow a doctor access to patient records only from secure hospital devices and only during work hours.
- Edge Case: While ABAC offers flexibility, it can become complex to manage when there are many attribute variables across a large organisation. Automation tools or policy engines help manage this complexity.
Quick Takeaway: Start with clear attribute definitions to avoid policy conflicts, and consider automating policy updates to keep access rules manageable as your organisation scales.
2. Contextual or Risk-Based Access
Contextual access control, also called risk-based access, evaluates the context of an access request and adjusts the security level based on factors such as behaviour, device health, and network location. Contextual access strengthens security, especially in high-risk scenarios, by dynamically enforcing stricter policies.
- Example: A finance company may allow employees to access sensitive data from secure networks but require MFA for the same data if accessed from an external network.
- Analogy: Contextual access is like letting someone into an office only during business hours, adjusting based on real-time conditions like time and location.
- Implementation Tip: Start by defining the highest-risk access scenarios, such as external network access, and apply stricter controls before expanding to other contexts.
Quick Takeaway: Contextual access provides flexibility in access policies while prioritising security in riskier situations, making it ideal for hybrid cloud setups where users work in multiple environments.
3. Role-Based Access Control (RBAC) with Attribute Enhancements
RBAC can be adapted for hybrid environments by augmenting it with additional attributes or contextual policies. This allows the broad structure of RBAC to remain while implementing more granular access controls.
- Example: An IT admin may have access to system settings generally, but policies can restrict access to sensitive areas based on real-time checks like device health.
- Implementation Tip: Set up “least privilege” roles in your RBAC system, then apply conditional access policies to add further restrictions as needed.
Quick Takeaway: Using RBAC as a foundation, attribute-enhanced RBAC provides both structured and granular access that adapts to the changing requirements of hybrid cloud environments.
4. Unified Identity and Access Management (IAM)
Unified IAM centralises access management across different environments, streamlining authentication and authorisation processes for all users. By integrating various cloud providers and on-premises systems, IAM ensures consistent, centralised management of access policies across platforms.
- Example: Tools like Okta, Ping Identity, or Azure AD provide SSO for users across cloud and on-premises environments.
- Edge Case: For organisations with legacy systems, integrating all platforms into a unified IAM framework may require additional customisations and support from identity providers.
Quick Takeaway: Unified IAM simplifies access control, particularly for hybrid cloud environments, providing consistent access policies and better security visibility.
5. Zero Trust Network Access (ZTNA) Principles
ZTNA enforces “never trust, always verify,” requiring continuous verification for every access request, regardless of location. By implementing ZTNA in a hybrid cloud environment, organisations can secure data flows and ensure access requests are authenticated and authorised continuously.
- Example: In a hybrid cloud, ZTNA might require users to authenticate frequently when switching between environments, granting access based on verified identity and secure device status.
- Real-World Tip: Use ZTNA tools like Zscaler Private Access or Palo Alto Networks Prisma Access, which support hybrid cloud environments.
Quick Takeaway: ZTNA provides a robust framework for securing hybrid clouds, offering seamless, secure access without complex VPN setups.
Tools for Enforcing Fine-Grained Access Controls
A variety of tools support fine-grained access control across hybrid clouds. Here’s an overview of key solutions:
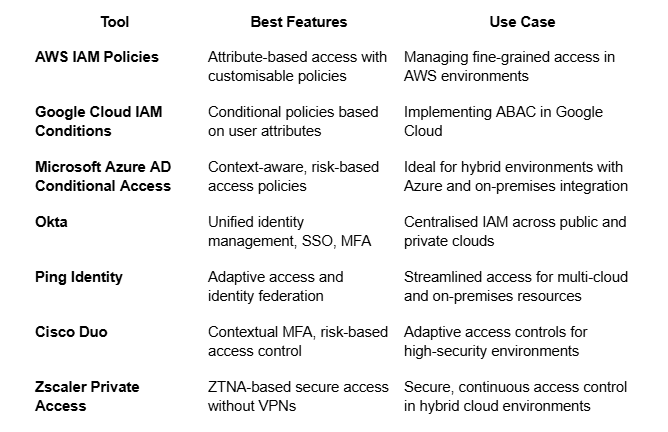
Key Takeaway: The right tools simplify fine-grained access control in hybrid clouds, and multi-functional tools that integrate IAM, contextual policies, and adaptive access control offer the most streamlined approach.
Best Practices for Enforcing Fine-Grained Access Controls
To ensure effective enforcement of fine-grained access controls in hybrid clouds, consider the following best practices:
1. Implement Least Privilege Access
Limit each user’s access to only the resources necessary for their role, minimising potential exposure to unauthorised users.
- Actionable Tip: Conduct quarterly access reviews to remove outdated permissions and maintain least privilege.
2. Use Multi-Factor Authentication (MFA) for All Privileged Access
MFA prevents unauthorised access by adding an additional verification layer, especially for high-privilege accounts.
- Real-World Tip: Consider using risk-based MFA to dynamically adjust verification levels based on context, like location or device health.
3. Monitor and Audit Access Continuously
Implement continuous monitoring of access requests and log all activities for auditing purposes.
- Actionable Tip: Use monitoring tools like Splunk or Azure Sentinel to flag unusual access patterns and respond proactively.
4. Regularly Update and Test Access Policies
Regular policy updates and testing are essential to meet evolving security standards and maintain effective access controls.
- Quick Takeaway: Schedule policy audits at least quarterly, and test policies to ensure they work seamlessly across hybrid environments.
5. Encrypt Data at Rest and in Transit
Encryption ensures that sensitive information is protected, even if access controls are bypassed.
- Implementation Tip: Use native encryption tools from your cloud provider, like AWS KMS or Google Cloud Key Management, to secure data in all environments.
Conclusion
Enforcing fine-grained access controls across hybrid clouds is crucial for securing distributed resources, meeting regulatory standards, and preventing unauthorised access.
By combining ABAC, contextual and risk-based access, RBAC, unified IAM, and ZTNA principles, organisations can implement flexible, dynamic policies that address the complexities of hybrid environments.
Using the right tools and following best practices enhances security, operational efficiency, and compliance, creating a resilient hybrid cloud infrastructure that minimises risk and supports organisational agility.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand



