Enforcing Risk-Based Conditional Access: Detecting and Mitigating Anomalous Login Behavior in Hybrid Environments

Introduction
In today’s hybrid work environments, organisations face the challenge of securely managing access for employees logging in from diverse locations and devices. As the modern workforce blends remote and in-office access, traditional access management solutions based on static rules and role-based access control (RBAC) no longer provide sufficient protection.
In response, many organisations are adopting risk-based conditional access to monitor login behaviour in real time, detect anomalies, and take immediate action when suspicious activity is identified.
Risk-based conditional access enables organisations to analyse contextual information around each login attempt, dynamically adjusting access requirements based on risk levels. This approach not only enhances security by flagging unusual behaviour but also preserves user experience by avoiding unnecessary roadblocks when risk levels are low.
In this article, we’ll explore the mechanics of risk-based conditional access, strategies for detecting anomalous login behaviour, and techniques for mitigating potential threats.
What is Risk-Based Conditional Access?
Risk-based conditional access refers to the practice of applying access controls based on real-time risk assessments. Unlike traditional access controls, which rely on predefined roles or static conditions, risk-based access policies evaluate factors like the user’s location, device health, login patterns, and other contextual elements to determine the risk associated with each access request. This dynamic approach allows organisations to respond flexibly, increasing security requirements only when risk indicators warrant it.
Core Elements of Risk-Based Conditional Access:
- User and Device Context: Considers the user’s role, permissions, and the health of the device they are using (e.g., personal vs. corporate, secure vs. insecure).
- Behavioural Analytics: Tracks historical login behaviour to detect deviations from the norm, such as unusual time, location, or device.
- Location Data: Identifies trusted and untrusted locations, limiting or challenging access from risky areas.
- Real-Time Risk Scoring: Calculates a risk score based on the analysis of the above factors, triggering additional verification steps or restrictions when risk is high.
Example in Practice: A risk-based conditional access system may allow a finance employee logging in from their usual device and location to proceed without interruption. However, if the same employee attempts to log in from an unusual country, the system could require additional verification, like multi-factor authentication (MFA), before granting access.
Importance of Detecting Anomalous Login Behavior
In hybrid work environments, detecting anomalous login behaviour is crucial for maintaining security without disrupting legitimate access. Anomalous behaviour can indicate various potential threats, including account compromise, phishing attacks, and credential stuffing. However, accurately distinguishing between legitimate and malicious access attempts is challenging, especially as users frequently access systems from multiple devices and locations.
Common Anomalous Login Indicators:
- Unusual Location: Logins from unfamiliar geographic locations, especially those outside the user’s normal access areas, can signal compromise.
- New or Untrusted Device: Attempts to log in from a device that has not previously been associated with the user’s account.
- Unusual Time of Access: Login attempts outside of standard working hours, especially for users with established patterns, may be suspicious.
- High Velocity of Login Attempts: Multiple login attempts from different locations within a short timeframe can suggest a “man-in-the-middle” attack or credential stuffing.
By establishing a baseline of normal behaviour for each user and monitoring deviations, risk-based conditional access can identify potential threats early and enforce additional security measures as needed.
Strategies for Detecting Anomalous Login Behavior
Implementing effective anomaly detection requires a multi-faceted approach that combines data analytics, machine learning, and pre-defined conditions. Here are some key strategies:
1. Behavioural Baselines
Behavioural baselining involves monitoring user activity over time to establish a pattern of normal behaviour. By tracking variables like login time, location, device type, and frequency, organisations can detect deviations that indicate anomalous activity.
Think of it this way: Baselines help define what “normal” looks like, so anything unusual can be flagged for further review.
- Example: If an employee who usually logs in from New York suddenly accesses the system from Hong Kong, the system can flag this as an anomaly.
- Implementation Tip: Start by setting up baseline profiles for high-risk roles, such as administrators, and refine profiles as more data is collected.
2. Geo-Location Tracking
Geo-location tracking enables organisations to restrict or challenge access based on the user’s physical location. By categorising certain regions as high-risk or trusted, organisations can apply additional authentication requirements or deny access outright when login attempts come from unfamiliar or risky areas.
Location-based tracking is like checking a visitor’s ID at the door: If they’re from a trusted neighbourhood, they enter freely. If they’re from an unknown area, they get an extra check.
- Real-World Tip: Use geo-fencing to automatically challenge access requests from outside defined trusted regions, reducing the risk of unauthorised access from untrusted locations.
Quick Takeaway: Establish trusted regions to streamline access for frequently used locations, while adding more robust checks for unfamiliar access points.
3. Device Health Monitoring
Device health monitoring evaluates the security status of the user’s device, checking for factors like operating system version, security patches, and anti-virus status. This information is crucial in hybrid environments, where users may access resources from both personal and corporate devices.
Think of it this way: Devices are like different doors to your organisation, and each door requires a unique key depending on its security status.
- Example: Access from an outdated personal device may trigger a requirement for MFA, while a well-maintained corporate device with up-to-date security patches could proceed without additional verification.
- Edge Case Consideration: For organisations with both corporate-owned and bring-your-own-device (BYOD) models, consider creating separate policy categories. Corporate devices may pass through with fewer restrictions, while BYOD devices can trigger additional verification steps.
- Implementation Tip: For BYOD setups, start with less restrictive policies but increase requirements for older devices or those without recent patches.
4. Velocity Monitoring
Velocity monitoring detects the speed and volume of login attempts, flagging high-frequency access attempts as potential credential stuffing or brute-force attacks. High-velocity monitoring is especially useful for identifying automated attacks where attackers attempt multiple logins in a short time.
Implementation Tip: Limit login attempts by geography to prevent “impossible travel” scenarios, where multiple access attempts appear from distant locations within minutes.
- Example: If multiple login attempts are made from different IP addresses within minutes, velocity monitoring can detect this as unusual and require additional verification or temporarily block access.
Quick Takeaway: Keep login attempts at a manageable rate by detecting abnormal velocity and adding verification layers.
Mitigating Anomalous Login Behavior
Once an anomaly is detected, risk-based conditional access can take several actions to mitigate potential threats. Here’s an overview of common responses:
1. Multi-Factor Authentication (MFA) Challenges
Triggering MFA when anomalous behaviour is detected adds a layer of security by requiring users to provide a second form of verification. This method is particularly effective for access attempts from new devices or locations, as it allows legitimate users to verify their identity while preventing unauthorised access.
Analogy: Think of risk-based access as a thermostat that adjusts the temperature automatically based on the surrounding conditions. It adapts security requirements depending on the user’s context, responding to changes in access patterns as they arise.
- Example: An administrator logging in from a new device would need to complete an MFA challenge before proceeding.
- Implementation Tip: Set up MFA challenges only for high-risk scenarios to maintain a seamless user experience.
2. Session Restrictions and Conditional Timeouts
Session restrictions and timeouts allow organisations to limit access duration based on risk levels. For example, if an anomaly is detected mid-session, the system can terminate or restrict the session to reduce potential data exposure.
- Example: If an employee’s location suddenly changes during a session, a conditional timeout can end the session and require re-authentication.
- Best Practice: Implement session monitoring tools that track active sessions and enforce timeouts when anomalies are detected.
Quick Takeaway: Using session restrictions helps contain risks without the need for immediate user intervention, making it an efficient way to protect data during anomalous events.
3. Real-Time Alerts and Risk Scoring
Risk-based conditional access systems often use real-time alerts and risk scoring to prioritise security responses. By calculating a risk score based on contextual data, the system can determine whether additional authentication, restricted access, or an outright block is necessary.
Imagine a bouncer at a club: As people approach, the bouncer quickly evaluates each person to decide who needs extra screening. Real-time risk scoring does something similar with login attempts, allowing only the low-risk to proceed smoothly.
- Example: A login attempt with a high-risk score due to unusual location, untrusted device, and high velocity may trigger an automatic block and alert security teams for further investigation.
- Nuanced Tip: Begin by identifying the highest-risk areas where real-time alerts add the most value, and configure risk scoring thresholds based on access sensitivity.
Quick Takeaway: Real-time alerts keep security teams informed and ready to respond, while risk scoring helps prioritise actions based on threat levels.
Best Practices for Implementing Risk-Based Conditional Access
To effectively implement risk-based conditional access, organisations should follow several best practices:
1. Use the Principle of Least Privilege
Limit each user’s access to only the resources necessary for their role. This approach not only minimises risk but also reduces the likelihood of anomalous access from unused accounts or excessive permissions.
- Actionable Tip: Conduct quarterly reviews of user permissions to remove any outdated or unnecessary access.
2. Apply Layered Authentication for High-Risk Users
Multi-layered authentication, such as risk-based MFA, provides an added level of protection for users in high-risk roles, like system administrators. MFA challenges should adapt based on risk levels and historical access patterns.
- Example: System admins may have to re-authenticate periodically or when accessing particularly sensitive resources.
3. Integrate Contextual Access with Unified IAM
Integrating conditional access policies into a unified IAM (Identity and Access Management) platform allows for seamless application of rules across cloud, on-premises, and hybrid environments. This unified approach reduces complexity and enhances consistency.
- Real-World Tip: Use tools like Microsoft Azure AD Conditional Access or Okta to centralise policy management and streamline IAM across all environments.
4. Monitor and Adjust Policies Continuously
Risk-based conditional access policies need regular review and adjustment to keep up with emerging threats and changing user behaviour. Ongoing monitoring helps organisations refine policies based on real-world insights and audit results.
- Actionable Tip: Schedule quarterly audits to assess policy effectiveness and adjust rules as new security requirements emerge.
5. Ensure Transparency and Communication with Users
Clear communication with users about the conditions that may trigger additional verification can improve user compliance and reduce friction. Informing users of policy updates, especially around MFA and location-based access, promotes cooperation.
Key Takeaway: Transparent communication improves user experience and strengthens security policy adherence across the organisation.
Tools for Enforcing Risk-Based Conditional Access
Several tools can help implement risk-based conditional access, each offering different features to enhance security in hybrid environments:
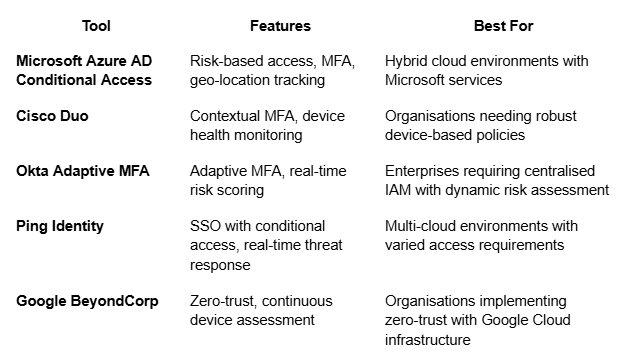
Quick Takeaway: Choosing the right tool depends on your organisation’s infrastructure and specific access control needs, with options available to suit hybrid, multi-cloud, and zero-trust architectures.
Real-World Applications of Risk-Based Conditional Access
Risk-based conditional access has become an essential strategy across industries. Here are some examples:
- Financial Services: Financial institutions can use behavioural baselines to monitor employees’ access to sensitive client information. Attempts to log in from untrusted devices or unusual locations may trigger MFA, ensuring only verified access.
- Healthcare: Hospitals use conditional access to limit access to patient records based on location. For example, healthcare workers may access records from within the facility’s network, but off-site access requires additional verification to prevent data breaches.
Added Industry Examples:
- Government Sector: In government institutions, geo-location policies can enforce strict access controls, limiting high-risk data access to designated buildings.
- Retail Industry: For retail, conditional access can restrict payment system access to secure, known devices, lowering the risk of fraudulent transactions.
Conclusion
Enforcing risk-based conditional access is critical for managing security in hybrid environments, where login behaviour is more dynamic and diverse. By monitoring and responding to anomalous login behaviour, organisations can safeguard data and prevent unauthorised access without impacting legitimate user experiences.
Through the use of behavioural baselines, device health monitoring, and geo-location tracking, risk-based conditional access provides a flexible, dynamic approach to access management. With regular policy adjustments and user transparency, organisations can stay agile, secure, and resilient in today’s ever-evolving digital landscape.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand



