As more organisations move critical infrastructure to Google Cloud Platform (GCP), one thing becomes clear: It’s not enough to trust that everything’s secure out of the box.
Even with Google’s best practices in place, misconfigurations can sneak in, privileges can expand unnoticed, and threat actors never stop evolving.
That’s where GCpwn comes in. It’s an open-source penetration testing (pentesting) toolkit built specifically for GCP environments. GCpwn helps you simulate real-world attacks, audit your IAM setup, and uncover potential weaknesses - before someone else does.
This guide walks through how to set up GCpwn, where it adds value, and how teams are using it to close gaps in their cloud security posture.
1. Why Pentest GCP in the First Place?
Google’s infrastructure is battle-tested, but the shared responsibility model still applies: Google secures the platform, but it’s on you to secure your configuration - permissions, services, data, and APIs.
So why bother with a GCP-specific pentesting tool?
- Misconfigurations are common. All it takes is one overly permissive role or open port.
- Attackers are proactive. New methods to exploit cloud environments are emerging faster than ever.
- Compliance may require it. Many industries mandate regular pentesting to validate cloud security controls.
GCpwn helps teams expose hidden risks in their environment before those risks become incidents.
2. Meet GCpwn: What It Does and Why It’s Useful
GCpwn is tailored for GCP environments, making it more effective than general-purpose security tools.
It’s designed to simulate attacker behaviour in a controlled way, giving you insight into how
your setup would hold up under pressure.
Here’s a snapshot of what it can do:
- IAM Role Audits: Identify risky permissions, including overly broad or inherited roles.
- Firewall Testing: Scan for open ports or rules that allow unrestricted access.
- Cloud Storage Checks: Detect public buckets or weak ACLs and surface encryption gaps.
- Service Exploits: Simulate attacks on GCP services like Cloud Functions or GKE.
It’s practical, flexible, and built to answer the question: “What could go wrong here - and how would I know?”
3. How to Set Up GCpwn in Your GCP Environment
Getting started with GCpwn is straightforward, especially if you’re familiar with Python and the GCP CLI.
Step-by-Step Setup
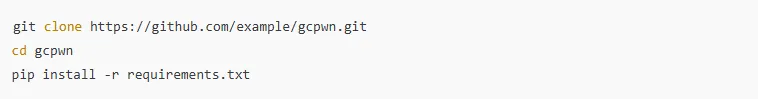
Step 1: Install the Tool
- First, clone the GCpwn repository:
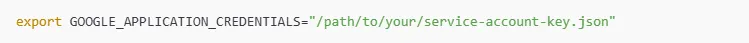
Step 2: Configure GCP Credentials
GCpwn needs to query your environment, so create a service account with permissions such as Viewer, Security Reviewer, and IAM Auditor.
Download the key file and export it like this:
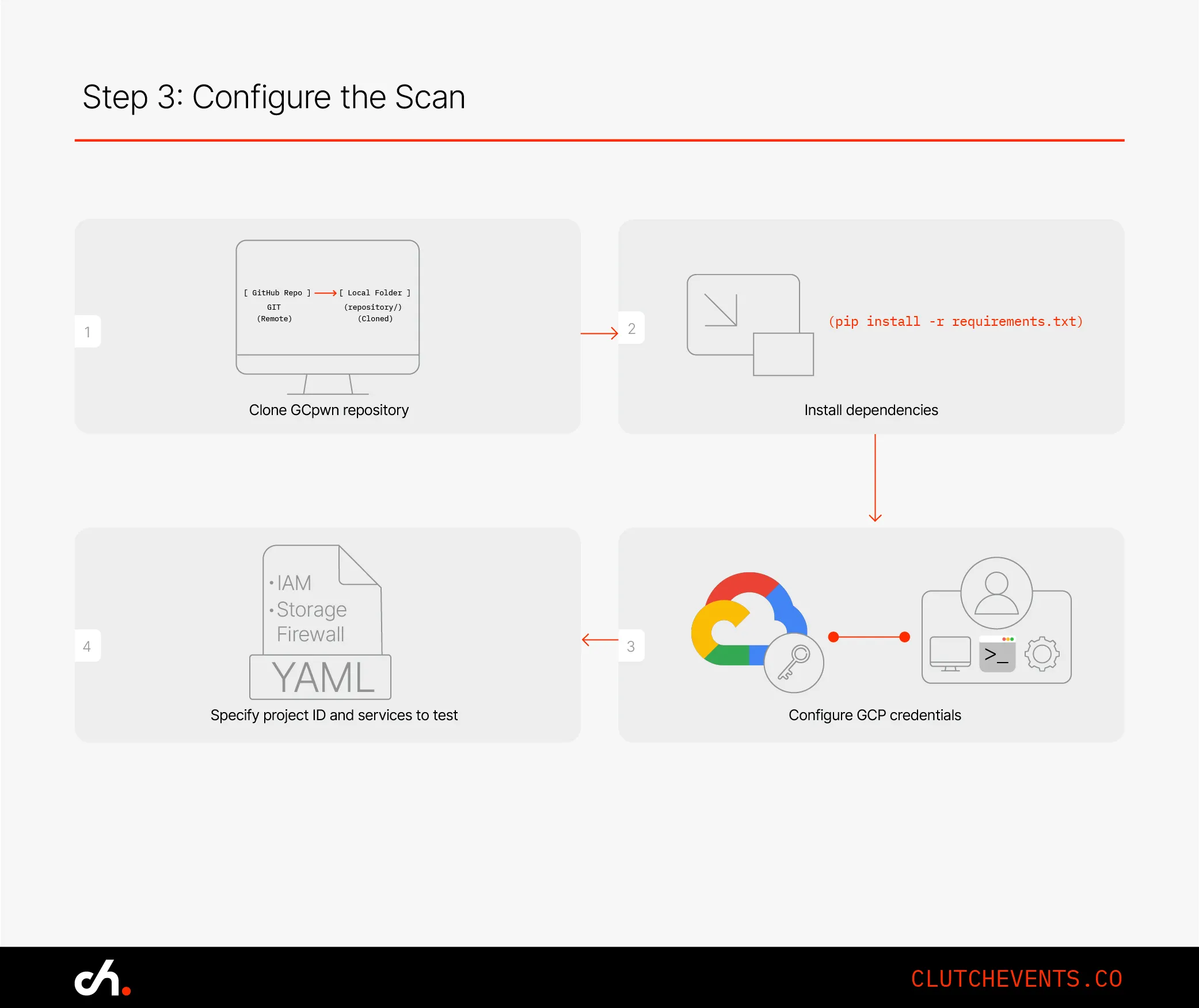
Step 3: Configure the Scan
Edit the config.yaml file to specify which GCP project and services you want to test - like IAM, Cloud Storage, or Firewall rules. Then save and run your first scan:

Tip: Run it in a test or staging environment first to avoid any unintended disruptions.
4. Where GCpwn Shines: Common Use Cases
GCpwn is pretty flexible and can be used in different ways depending on what you need. Here are some common use cases that can really help beef up your GCP security.
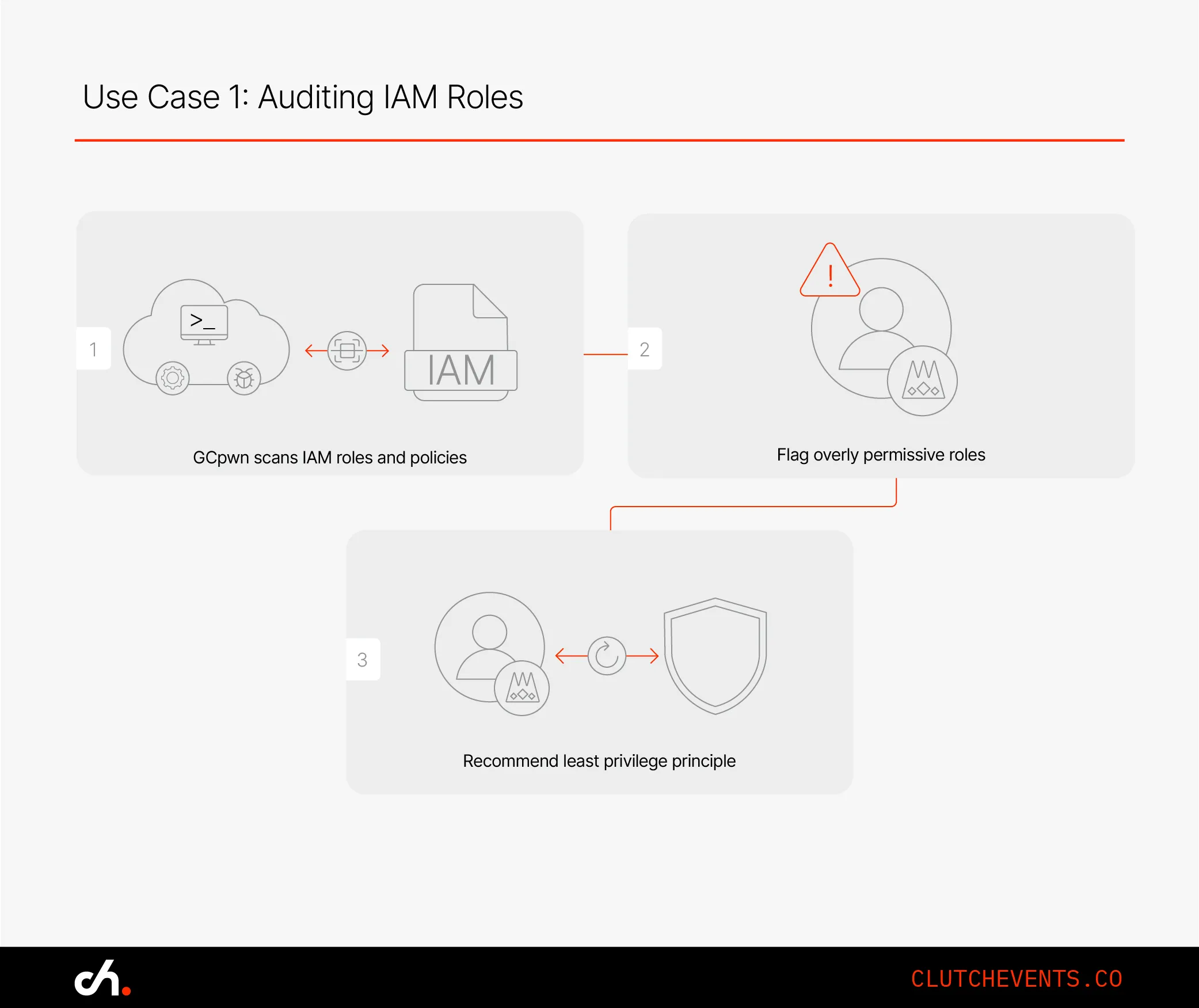
Use Case 1: Auditing IAM Roles
GCP IAM is flexible - but that flexibility can lead to privilege creep. GCpwn scans for roles that are overly permissive or inconsistent with least privilege.
Example: A user was mistakenly given Owner access across a project. GCpwn flagged it, and the team replaced it with a narrower, role-based permission - preventing accidental privilege escalation.
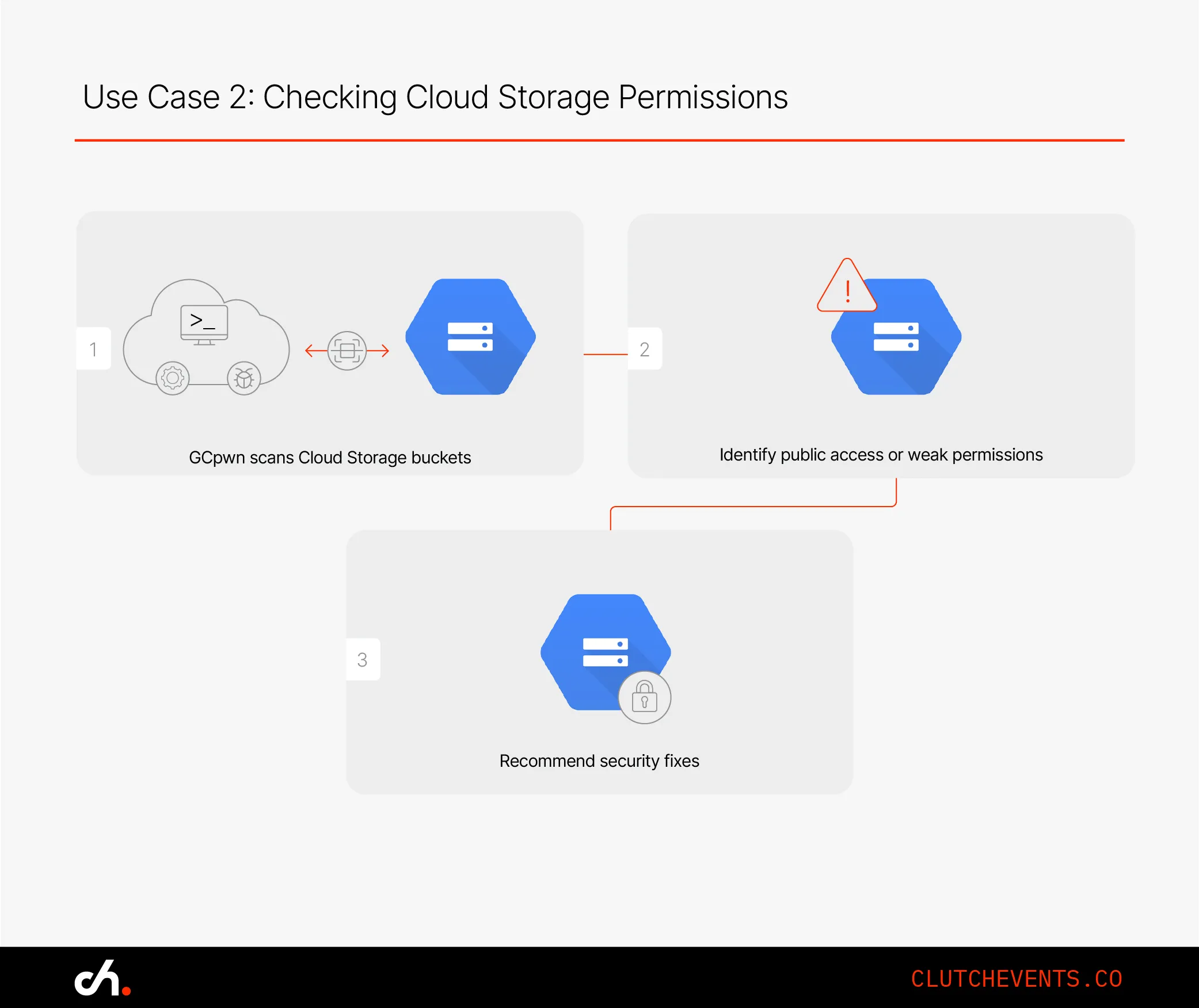
Use Case 2: Checking Cloud Storage Permissions
Public buckets continue to be a major risk in cloud breaches. GCpwn detects storage buckets that allow public access or have weak ACLs.
Example: During a routine scan, a team discovered that a forgotten test bucket with internal PDFs was accessible via a public URL. GCpwn surfaced the issue before anyone else found it.
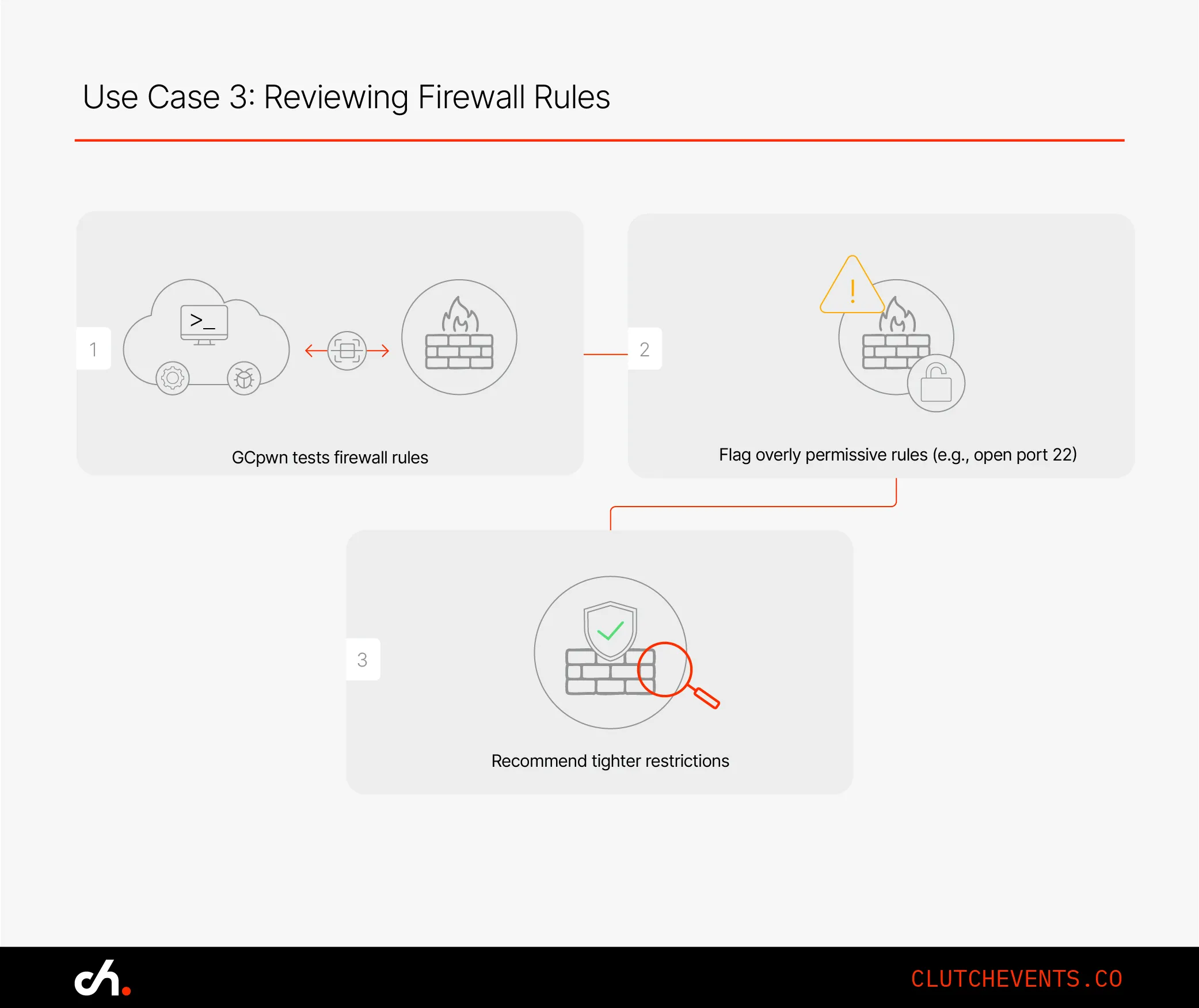
Use Case 3: Reviewing Firewall Rules
Excessive exposure through the network layer is another common misstep. GCpwn can review firewall configurations and call out overly broad rules.
Example: SSH (port 22) was open to all IPs. GCpwn flagged it, and access was immediately limited to the corporate IP range.
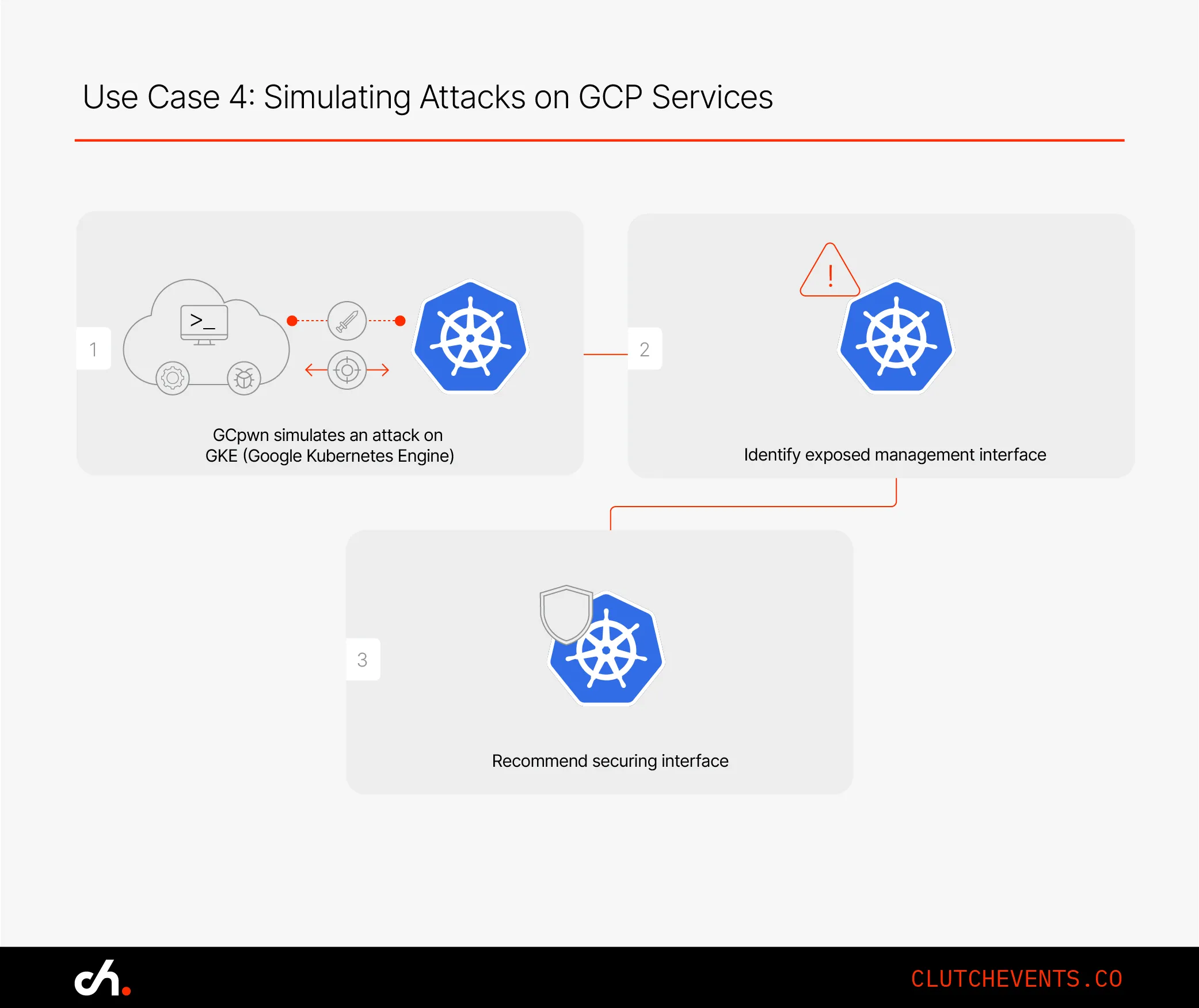
Use Case 4: Simulating Attacks on GCP Services
GCpwn includes modules that simulate attacker behaviour against GCP services like Kubernetes clusters, App Engine apps, and Cloud Functions.
Example: A GKE cluster’s dashboard was found to be exposed without authentication. GCpwn detected the risk, and the team hardened access control immediately.
5. Best Practices for Using GCpwn
Getting value from GCpwn means running it thoughtfully. Here are a few guidelines to follow:
- Use a staging environment first: Avoid disruption by testing configurations outside of production.
- Keep it updated: GCpwn evolves alongside GCP. Regularly update your clone to benefit from new modules or bug fixes.
- Integrate it into CI/CD: Trigger scans on deployment events to catch new misconfigurations early.
- Layer with other tools: Pair GCpwn with GCP’s Security Command Center or open-source tools like Cloud Custodian for deeper insights.
6. Real-World Wins: What GCpwn Has Found
A few anonymised examples from teams in the field:
- Case 1: GCpwn uncovered a backup storage bucket that had been publicly exposed for weeks, missed by native monitoring tools.
- Case 2: A pentest revealed that several service accounts had permission scopes far broader than needed, opening the door for lateral movement.
- Case 3: During a red-team simulation, GCpwn helped demonstrate how misconfigured functions in Cloud Run could be chained for privilege escalation.
In each case, GCpwn gave teams the data they needed to act, before anyone else could exploit the gaps.
Final Thoughts
Cloud platforms like GCP make it easy to move fast, but that speed can come at a cost if you’re not careful. GCpwn helps security teams slow down just long enough to test, inspect, and harden their setup before it becomes an issue
Whether you're auditing IAM policies, scanning firewall rules, or poking at Kubernetes clusters, GCpwn gives you a GCP-native way to stay ahead of misconfigurations and security drift.
Add it to your toolkit - and make pentesting part of your normal cloud hygiene.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand




