OAuth Token Replay Attacks: How to Detect and Defend in Distributed Cloud Environments

Introduction
With the rise of distributed cloud environments, organisations are increasingly using OAuth tokens to manage secure authentication and authorizsation for users and services. While OAuth tokens are essential tools for granting access in a secure, scalable way, they also introduce vulnerabilities - specifically, they can be intercepted and misused in what’s known as a replay attack. In a replay attack, an attacker intercepts a valid token and reuses it to gain unauthorised access to sensitive resources.
As cloud infrastructures grow more complex and interconnected, defending against replay attacks has become crucial for identity and access management (IAM) teams.
In this article, we’ll explore the mechanics of OAuth token replay attacks, the vulnerabilities they exploit, detection strategies, and effective defense mechanisms. Real-world tools and practices for multi-cloud implementations are also included to help IAM professionals design a secure, resilient token management system.
Understanding OAuth Token Replay Attacks
OAuth token replay attacks are unique in that they rely on capturing an already validated token and then reusing it to gain unauthorised access. Unlike brute-force or phishing attacks, which often involve credential guessing, replay attacks take advantage of the token’s inherent validity. The authorisation server has already authenticated the token, so when the token is used again, it often grants access without re-verification.
How Token Replay Attacks Work
Think of token capture as the first step in any replay attack. It’s like someone ‘borrowing’ your ticket to re-enter an event without permission. Here’s a typical flow of how a token replay attack might unfold:
- Token Capture: The attacker captures a valid OAuth token, usually through man-in-the-middle attacks, insecure storage, or unencrypted transmission.
- Token Replay: With the captured token, the attacker can reuse it to access protected resources or services. Since the authorisation server has already validated the token, it often doesn’t require additional credentials, granting unauthorised access to the attacker.
- Persistence in Multi-Cloud Environments: In distributed or multi-cloud setups, tokens are often passed between platforms or services, increasing exposure and making them more susceptible to interception.
Example Scenario: In a multi-cloud environment, a user authenticates through an identity provider in Cloud A to access a service on Cloud B. If a token is intercepted during its transit between clouds, an attacker can use it to access the service on Cloud B without detection.
Quick Tip: Encrypt tokens in transit to prevent interception and add extra layers of security. Always use HTTPS for secure transmission, and periodically review network configurations.
Why OAuth Tokens Are Vulnerable to Replay Attacks
OAuth tokens have specific vulnerabilities that make them susceptible to replay attacks, especially in distributed environments where tokens pass between various cloud platforms.
1. Token Transmission Over Insecure Channels
When tokens are transmitted over insecure channels, such as HTTP or improperly configured HTTPS, they become vulnerable to interception. Distributed environments often involve different configurations and policies across clouds, increasing the risk of insecure transmission.
2. Long-Lived Tokens
Tokens with extended lifetimes, such as refresh tokens, provide a broader window for attackers to misuse them. While short-lived access tokens minimise this risk, frequent renewals can disrupt user experience, especially in services requiring prolonged access.
3. Lack of Sender-Constrained Tokens
OAuth tokens are generally bearer tokens, meaning that anyone who possesses the token can use it. Without sender-constrained tokens that tie a token’s validity to its original sender, attackers can easily reuse captured tokens.
4. Multi-Cloud Validation Gaps
Distributed cloud environments may have inconsistent token validation practices. If each cloud validates tokens differently, gaps can emerge, allowing unauthorised access. An attacker who obtains a token validated in Cloud A may be able to use it in Cloud B without additional checks.
Quick Tip: Consistent validation policies across clouds are crucial. Use identity federation tools to enforce cohesive validation standards, ensuring no cloud environment becomes a weak link.
Detection Strategies for OAuth Token Replay Attacks
Detecting token replay attacks requires analyzing patterns, identifying anomalies, and implementing robust logging. Here are key strategies to help with early detection:
1. Monitor for Anomalous Behavior
Detect unusual token usage patterns, like access from multiple locations or devices within a short period, known as “impossible travel.” This behavior often indicates that a token is being reused across different devices or locations.
- Example: If a token is used in rapid succession from geographically distant locations, it’s likely compromised. Monitoring systems can flag this behavior and trigger alerts for further investigation.
Quick Tip: Use ‘impossible travel’ detection to catch suspicious activity across distant locations in a short timeframe, alerting security teams to possible token misuse.
2. Track IP Addresses and Device Fingerprints
Associate tokens with specific IP addresses or device fingerprints. If a token is used from an unrecognised location or device, it can be flagged as suspicious and potentially blocked.
Real-World Example: Retail platforms can use IP and device binding to ensure only verified devices process transactions, reducing the risk of fraudulent token reuse in high-transaction environments.
3. Implement Rate Limiting and Velocity Checks
Rate limiting and velocity checks help prevent excessive token use within a short period. High usage frequency often signals a replay attack, especially if the same token is used repeatedly.
- Example: If a token accesses a resource 100 times within a minute, this activity likely indicates misuse. Rate limiting can flag such events for review.
4. Real-Time Alerting and Logging
Use real-time alerts and comprehensive logging to monitor token usage. Real-time alerts allow quick responses to suspicious behavior, while logs provide historical data for investigating past activity.
Quick Tip: Tools like Splunk and AWS CloudTrail are effective for setting up real-time alerts on unusual token activity, enabling immediate response and investigation.
Defense Mechanisms for OAuth Token Replay Attacks
Securing OAuth tokens involves proactive defense mechanisms throughout their lifecycle. Here’s how to fortify your token management practices:
1. Enforce HTTPS for Token Transmission
Using HTTPS for token transmission protects against interception and ensures data is encrypted between servers and clients. Even internal APIs should enforce HTTPS to prevent token theft.
2. Use Sender-Constrained Tokens
Sender-constrained tokens bind tokens to a specific device or IP address, making them unusable if intercepted. This added layer of protection restricts token usage to its original source.
- Implementation Tip: Use Proof of Possession (PoP) tokens or Mutual TLS (MTLS) to verify the sender’s identity each time the token is used. This ensures the token cannot be misused if intercepted by an attacker.
Real-World Example: Healthcare providers can bind tokens to specific devices, ensuring patient data is accessible only from authorised sources and meeting compliance needs.
3. Implement Short-Lived Access Tokens with Refresh Mechanisms
Short-lived tokens limit the exposure window, reducing the risk of token misuse. Refresh tokens allow users to obtain new tokens without re-authenticating, preserving security and user experience.
Example: Configure access tokens to expire within 10 minutes, while refresh tokens are only usable from secure networks or devices.
4. Restrict Token Scope to Minimise Damage
Token scopes define the resources and actions a token can access. By limiting scope, even a compromised token has minimal access, reducing the damage of a replay attack.
Quick Tip: Design tokens with the least privilege principle, ensuring they only access what’s necessary for the task.
5. IP Address and Device Binding
Binding tokens to specific IP addresses or devices limits their usability if intercepted and used from a different source. This approach prevents tokens from being reused in unauthorised ways.
Key Takeaway: Real-time monitoring is like having a security guard on duty 24/7, catching unusual behavior as soon as it happens. Combine HTTPS, sender constraints, and short token lifespans to prevent unauthorised token use.
Implementing Multi-Cloud Defense Practices
In distributed cloud environments, token management practices must be consistent across platforms to avoid vulnerabilities.
1. Centralise Identity Management
Imagine a single security checkpoint for all your clouds, centralising identity management helps you enforce consistent token policies across platforms. With a unified identity provider, token issuance, validation, and revocation can be centrally managed.
Tools: Providers like Okta, Azure AD, or Ping Identity support centralised token management, ensuring consistent security across clouds.
2. Use a Secure API Gateway
API gateways provide a trusted path for cross-cloud token validation. By validating tokens at a centralised gateway, organisations can ensure consistency across environments.
Implementation Tip: If using API gateways, ensure each gateway applies uniform token validation rules across clouds to avoid validation gaps.
3. Ensure Consistent Validation Across Clouds
Consistent token validation across cloud providers reduces the likelihood of exploitation. Use identity federation to enforce cohesive policies and ensure no environment becomes a weak link.
4. Implement Multi-Cloud Monitoring and Incident Response
Multi-cloud monitoring enables early detection of anomalies across platforms, and a unified incident response plan helps address suspicious activity efficiently.
Quick Tip: Real-time monitoring in distributed environments detects replay attacks across clouds before they escalate.
Tools and Technologies for Mitigating Replay Attacks
Here’s a quick comparison of tools and technologies that help secure OAuth tokens against replay attacks across distributed environments:
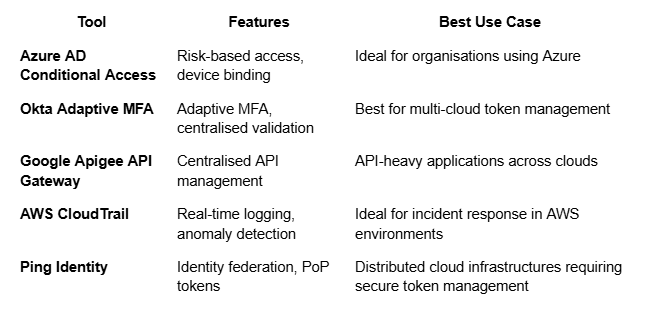
Summary of Key Takeaways
Detect Replay Attacks
- Monitor for Anomalous Patterns: Use IP and device monitoring, rate limiting, and impossible travel detection to identify suspicious token activity.
- Use Real-Time Alerts: Track unusual behavior promptly with tools like Splunk and AWS CloudTrail.
Secure Token Handling
- Use HTTPS: Transmit tokens over secure channels and use encryption to prevent interception.
- Implement Sender Constraints: Use PoP tokens or MTLS to bind tokens to their source.
Multi-Cloud Security
- Centralise Identity Management: Manage token validation and policies across clouds with a unified provider.
- Enforce Consistency: Apply uniform validation and monitoring practices to prevent gaps between environments.
By following these practices and implementing secure token management across multi-cloud platforms, IAM teams can protect against OAuth token replay attacks, enhancing security and resilience across their distributed infrastructures.
I apologize for that oversight. Here’s the conclusion section to add at the end:
Conclusion
OAuth token replay attacks are a significant risk in distributed cloud environments where tokens frequently move across multiple platforms. Attackers who capture these tokens can reuse them to gain unauthorised access, often bypassing standard authentication controls. Effective defense against replay attacks requires a blend of robust detection, proactive defense mechanisms, and consistent policies across clouds.
By enforcing secure token transmission through HTTPS, implementing sender-constrained tokens, and utilising short-lived access tokens, IAM teams can minimise token exposure. Monitoring for anomalous behavior, using IP and device binding, and centralising identity management in multi-cloud setups further strengthens these defenses. The use of API gateways and tools like adaptive MFA also enhances security, ensuring only legitimate users gain access to critical resources.
With these layered approaches, organisations can secure OAuth tokens more effectively, reduce the risk of replay attacks, and maintain a resilient IAM framework that supports seamless access and stringent security across cloud environments.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand



