Building a Global Compliance Framework for Cross-Border Data Transfers: Strategies for International Operations

Introduction
In today’s hyperconnected world, data flows across borders with ease, supporting everything from global ecommerce transactions to international collaborations. But with this movement of data comes a complex web of legal and regulatory obligations. Each country has its own rules on how data can be transferred and processed, and noncompliance can lead to hefty fines, reputational damage, or even a complete halt to business operations.
Building a robust compliance framework for crossborder data transfers isn’t just a box to tick. It’s a necessity for any business operating internationally. Take, for instance, a business expanding into a new market like Japan, only to realise shortly before launch that it must comply with the Act on the Protection of Personal Information (APPI). This kind of lastminute scramble is common. It highlights the importance of having a proactive and well structured compliance approach.
This briefing explores practical strategies for building and maintaining a global compliance framework that keeps your crossborder data transfers secure and legally sound, no matter where your organisation operates.
Understanding the Global Landscape of Data Protection Laws
If you manage data that crosses international borders, you’ve likely faced the challenge of staying compliant across multiple jurisdictions. Regulations differ significantly by region, and understanding the most influential ones provides a strong foundation for your compliance strategy.
General Data Protection Regulation (GDPR) - Europe
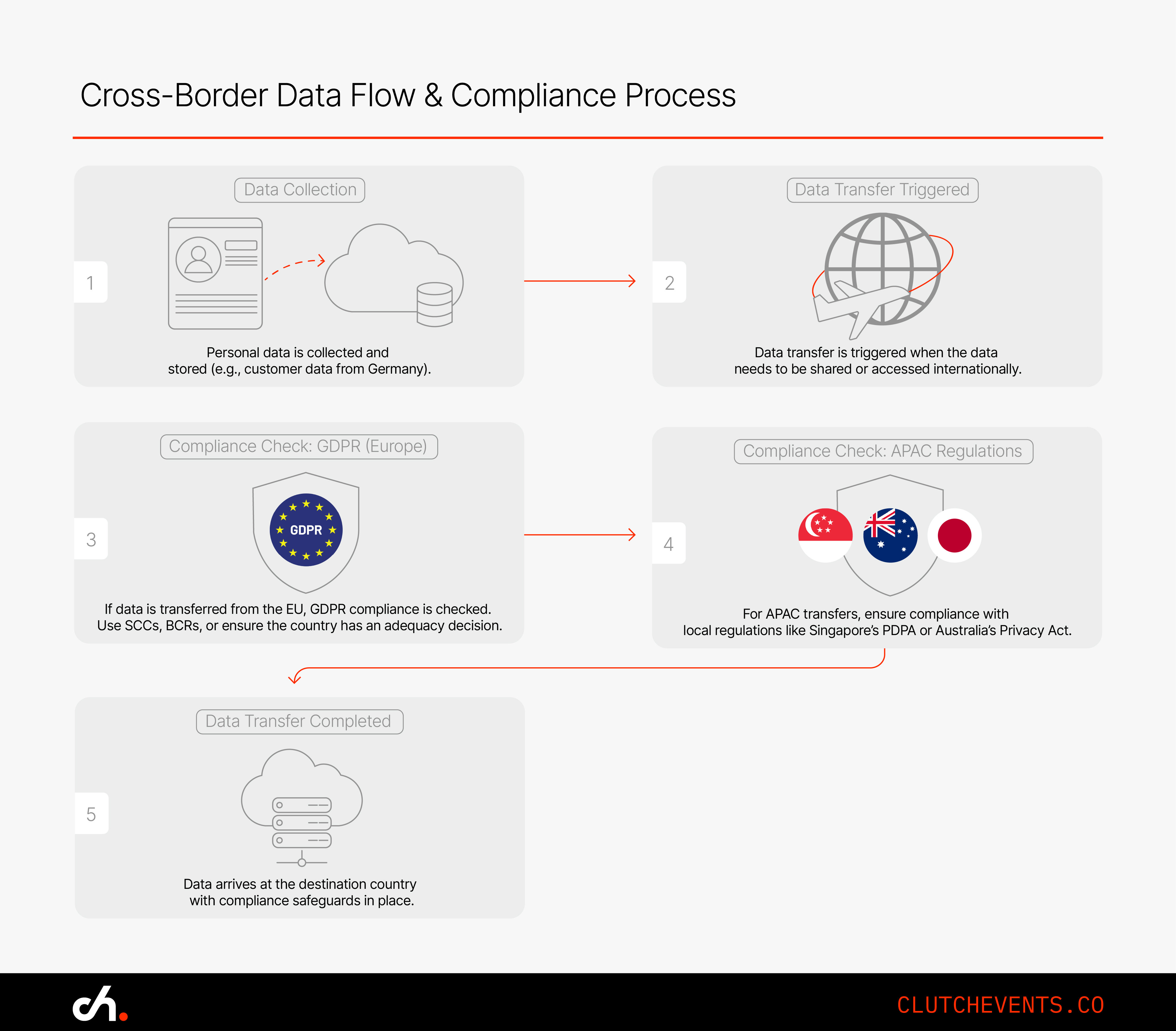
Europe’s GDPR applies to any business processing the personal data of EU citizens, regardless of where that business is based. The regulation is extraterritorial in scope, meaning a company in the US or Asia must still comply if it targets or handles data from the EU.
Key mechanisms for compliant transfers include:
- Adequacy Decisions: These allow for free data transfers to countries deemed to provide comparable levels of protection.
- Standard Contractual Clauses (SCCs): Legal templates approved by the European Commission for safeguarding data.
- Binding Corporate Rules (BCRs): Company-wide policies that enable intra-group international transfers.
Each mechanism requires ongoing effort. For example, SCCs must now be updated with new versions released by the European Commission in 2021, which include detailed obligations around onward transfers and access by public authorities.
Data Protection Regulations in APAC
The APAC region has a patchwork of laws that vary widely between countries:
- Singapore (PDPA) – Requires companies transferring personal data overseas to ensure a comparable level of protection.
- Australia (Privacy Act) – Obligates companies to ensure overseas recipients adhere to Australian privacy standards.
- Japan (APPI) – Mandates consent or equivalent safeguards for data sent to jurisdictions lacking adequacy.
In contrast to GDPR, many APAC laws are less prescriptive but still place a significant compliance burden on companies. For example, the PDPA includes data breach notification rules, while Australia has updated its Privacy Act to introduce stronger enforcement powers and expand the definition of personal information.
Example: A Japanese company transferring user data to the US must use SCCs or secure explicit consent to remain compliant.
The Rise of Data Localization Laws
Several countries now require that certain categories of data, especially personal or sensitive data, be stored or processed within national borders. This trend introduces major operational and cost implications for global businesses.
India’s Personal Data Protection Bill (PDPB), for example, mandates that sensitive personal data can only be transferred outside India under specific conditions and that critical personal data must be stored in-country. Similarly, China’s Personal Information Protection Law (PIPL) imposes restrictions on cross-border transfers and requires security assessments for large-scale data handling.
Example: Businesses expanding into these markets must consider whether their current infrastructure can support local data storage, which may involve working with regional cloud providers, building local data centres, or re-architecting key systems.
Key Components of a Global Compliance Framework
So, how do you ensure that your cross-border data transfers remain compliant in such a fragmented regulatory environment? The answer lies in building a global compliance framework. Let’s break down the essential components you need.
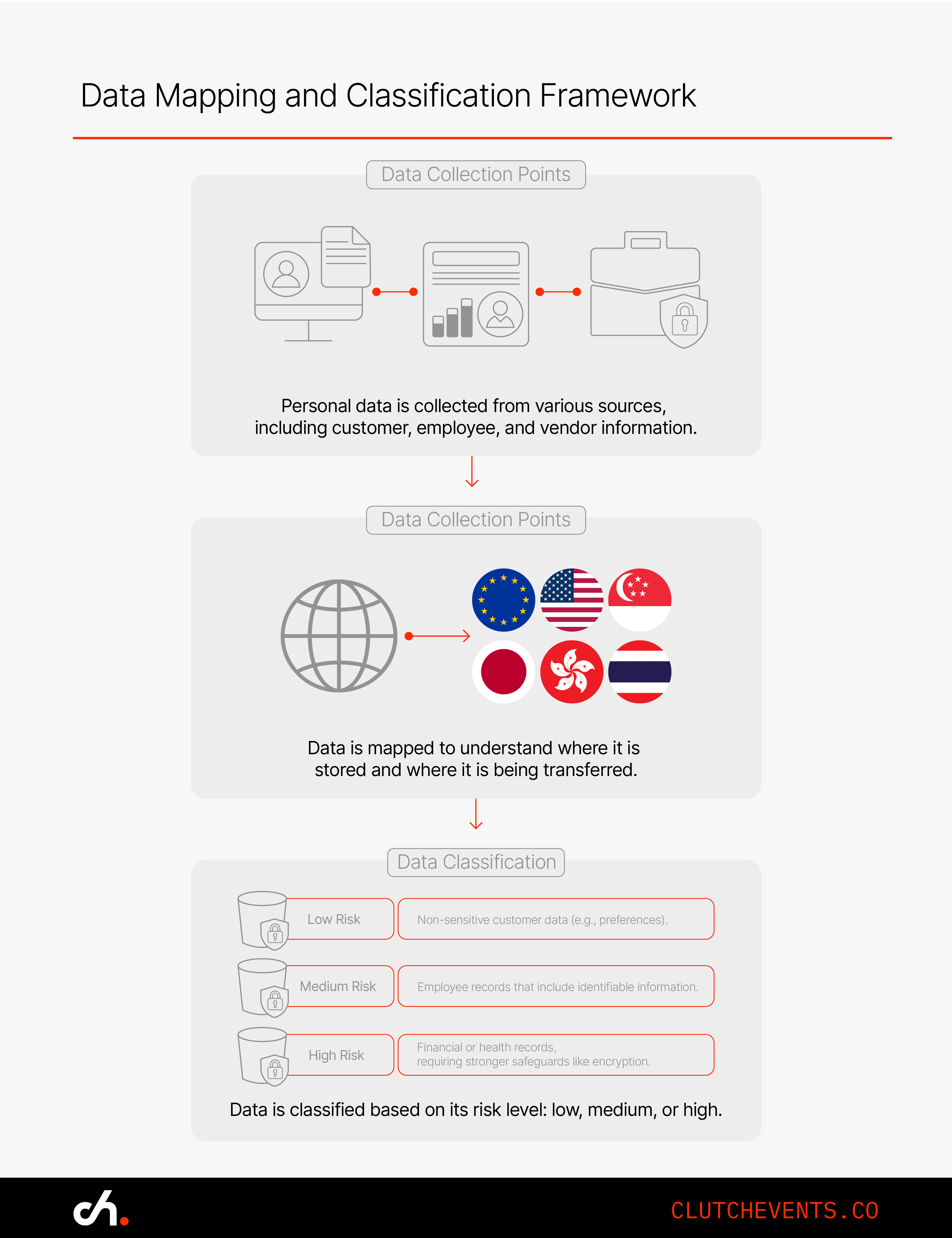
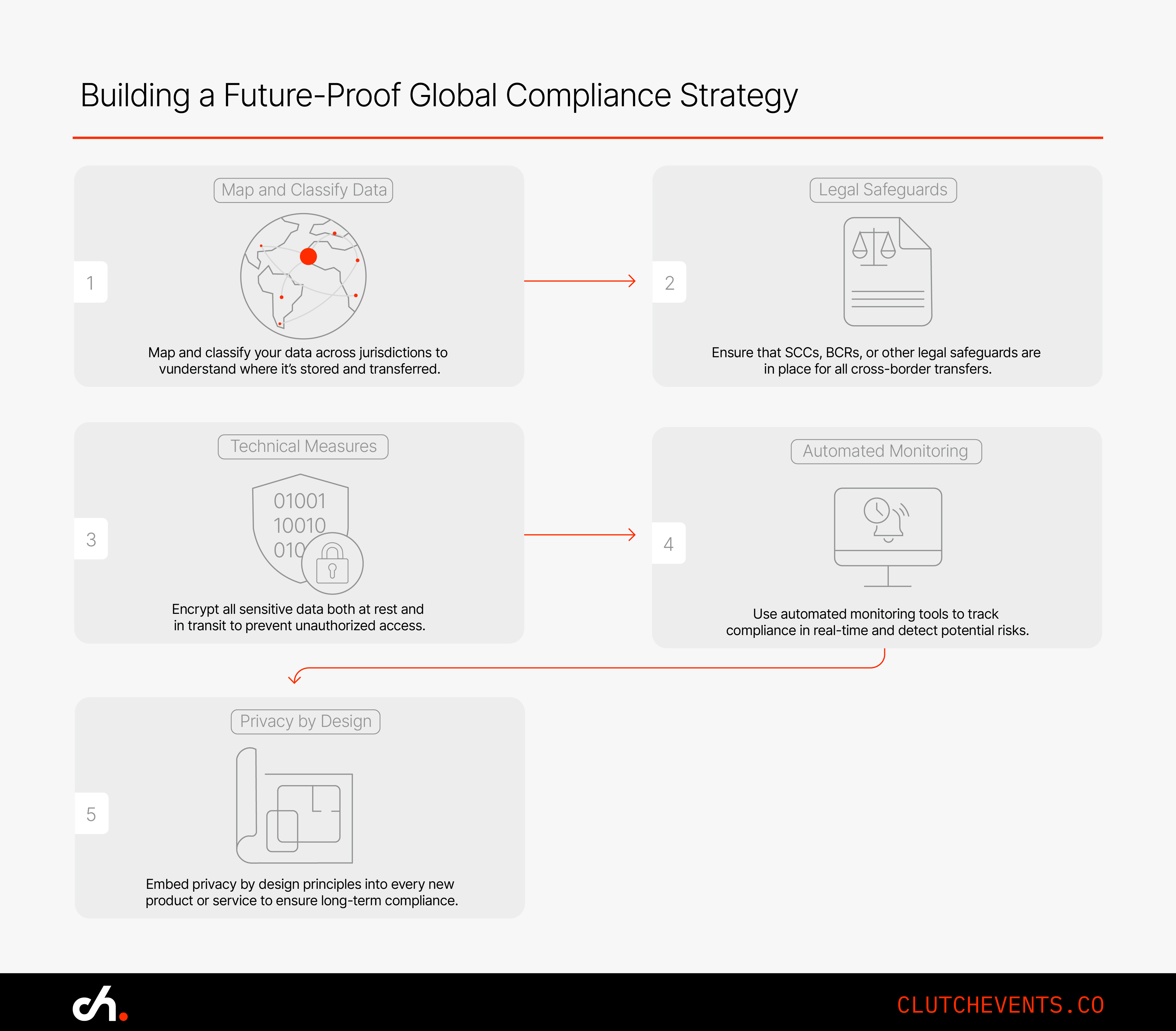
1. Data Mapping and Classification
You can’t protect what you don’t understand. Start by identifying and mapping all personal data including where it’s collected, processed, stored, and transferred.
Mapping should account for both structured and unstructured data and include all third-party processors. Once mapped, classify data by type and sensitivity.
Classify data according to risk:
- Low risk – User preferences, anonymous statistics
- Medium risk – Employee details, basic identifiers
- High risk – Health records, financial data, government-issued IDs
This classification helps determine what legal and technical safeguards are needed. It also enables more effective incident response and supports compliance with breach notification requirements.
Actionable Tip: Apply security controls and legal safeguards appropriate to each risk level.
2. Legal Assessments Across Jurisdictions
For each data flow, understand the legal implications in both the source and destination countries. Laws evolve for example, the Schrems II ruling, which invalidated the EU-U.S. Privacy Shield and changed how businesses transfer data across the Atlantic.
That ruling triggered a wave of reviews for existing contracts and forced businesses to assess the risk of surveillance or government access in receiving countries. Similar legal shifts may arise in other regions, meaning your compliance strategy needs to be both thorough and flexible.
Actionable Tip: Regularly review legal frameworks and updates in all regions where your data travels.
3. Contractual Mechanisms (SCCs and BCRs)
Where adequacy isn’t granted, use legally recognised agreements:
- SCCs: Provide immediate legal cover for cross-border transfers.
- BCRs: Offer long-term internal control for multinational data flows.
SCCs are commonly used with vendors or partners in third countries. BCRs are more complex to implement but provide scalable, regulator-approved compliance across a group of companies.
Example: A company with offices in Europe and Asia may rely on SCCs for vendor arrangements and BCRs internally.
4. Technical and Security Measures
Compliance must go hand in hand with robust technical controls:
- Encryption: Both in transit and at rest to ensure confidentiality.
- Access Controls: Use RBAC to enforce least privilege and reduce internal risk.
- Data Minimization: Reduce the volume of personal data processed or transferred.
Additional layers like intrusion detection systems, endpoint security, and secure coding practices also play a role. Security isn’t just about ticking a box, it’s about maintaining trust and ensuring business continuity.
Actionable Tip: Conduct regular audits of your technical defences to ensure they meet evolving best practices.
5. Monitoring, Auditing, and Ongoing Compliance
Compliance isn’t static. As your business expands or restructures, your data flows and associated risks change. That’s why real-time visibility and regular assessments are essential.
Tools that provide data lineage, transfer logs, and anomaly detection can help identify policy violations or unauthorised transfers. Regular audits also create a defensible record of due diligence.
Actionable Tip: Automate the monitoring of data flows and compliance checks to keep up with dynamic operations.
Strategies for International Operations
Building a compliance framework is just the first step. You also need strategies that allow your business to operate efficiently while staying compliant with local regulations.
1. Use of Regional Data Centers
Storing data closer to its point of collection simplifies compliance and reduces cross-border exposure. It also improves performance and localises support.
Cloud providers like AWS, Google Cloud, and Microsoft Azure all offer region-specific infrastructure that can help meet data residency requirements while scaling globally.
2. Cross-Functional Compliance Teams
Legal, IT, cybersecurity, and operations teams all have a role to play. A cross-functional approach ensures that data protection responsibilities are shared and that policies are implemented consistently.
These teams should meet regularly to review new risks, track evolving laws, and align on responses to regulatory changes or data incidents.
3. Privacy by Design
Bake privacy and security into new systems from the outset. It’s far more effective than retrofitting compliance after a product is built.
This includes conducting Data Protection Impact Assessments (DPIAs) before launching new initiatives, limiting the collection of personal data by default, and offering clear opt-in consent mechanisms.
Challenges in Global Compliance
Global compliance isn’t without its challenges. As data protection laws evolve and new regulations emerge, businesses will need to stay on top of these changes to ensure continued compliance.
1. Evolving Regulations
From GDPR updates to new laws like India’s PDPB or China’s PIPL, change is constant. What worked last year might not work now.
Tip: Track legal developments across all jurisdictions where you do business and subscribe to regional regulatory updates.
2. Data Localization Requirements
These can limit your ability to centralise infrastructure and may force investment in regional capabilities. Data sovereignty is becoming a national priority in many countries.
Tip: Partner with providers that support region-specific hosting and compliance. Include localization strategies in your infrastructure roadmap.
3. Third-Party Vendor Compliance
Outsourcing doesn’t shift responsibility. If your vendors mishandle data, you’re still liable.
Third-party risk assessments should cover data flows, sub-processors, and jurisdictional risks. Include right-to-audit clauses in contracts and require incident notification.
Tip: Add compliance clauses to contracts and perform due diligence on third-party practices.
Best Practices for Future-Proofing Your Compliance Framework
As global regulations continue to evolve, businesses need to future-proof their compliance frameworks to stay ahead of the curve.
1. Automate Compliance Monitoring
Use tools to continuously assess risks, detect anomalies, and produce audit-ready records. This enables faster response times and fewer surprises during inspections.
2. Privacy-Preserving Technologies
Pseudonymisation, anonymisation, and zero-knowledge encryption help balance utility and security. These techniques enable analytics and machine learning while maintaining regulatory compliance.
3. Regular Audits and Employee Training
A strong compliance culture starts with people. Train teams on evolving obligations and perform periodic audits to test resilience.
Interactive simulations and scenario-based training can improve awareness and help staff recognise and respond to risks.
Conclusion
Building a global compliance framework is no longer optional, it’s foundational to business continuity and customer trust. By aligning legal, technical, and operational strategies, businesses can stay ahead of the regulatory curve and ensure secure, scalable data operations across borders.
A proactive approach not only helps avoid fines. It also builds resilience, enables faster expansion into new markets, and signals trustworthiness to customers, investors, and partners.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand



