Developer-Focused Data Protection: Practical Steps for Security-First Code

In today’s fast-paced environment where innovation and data privacy are constantly colliding, developers are no longer just building features, they’re actively defending the integrity of the business. When deadlines pile up and pressure’s on, security can feel like a chore. But here's the truth: it’s not a checklist item. It’s a mindset. Secure code is the concrete slab under everything else. Without it, even the best-designed apps are vulnerable.
This guide walks through clear, practical ways to embed security thinking right into your workflow. It’s not about turning developers into security engineers, but helping teams build in protection where it matters most, which is early and often. Because let’s be honest: it’s much easier to fix a vulnerability in design than after the release candidate is live and the clock’s ticking.
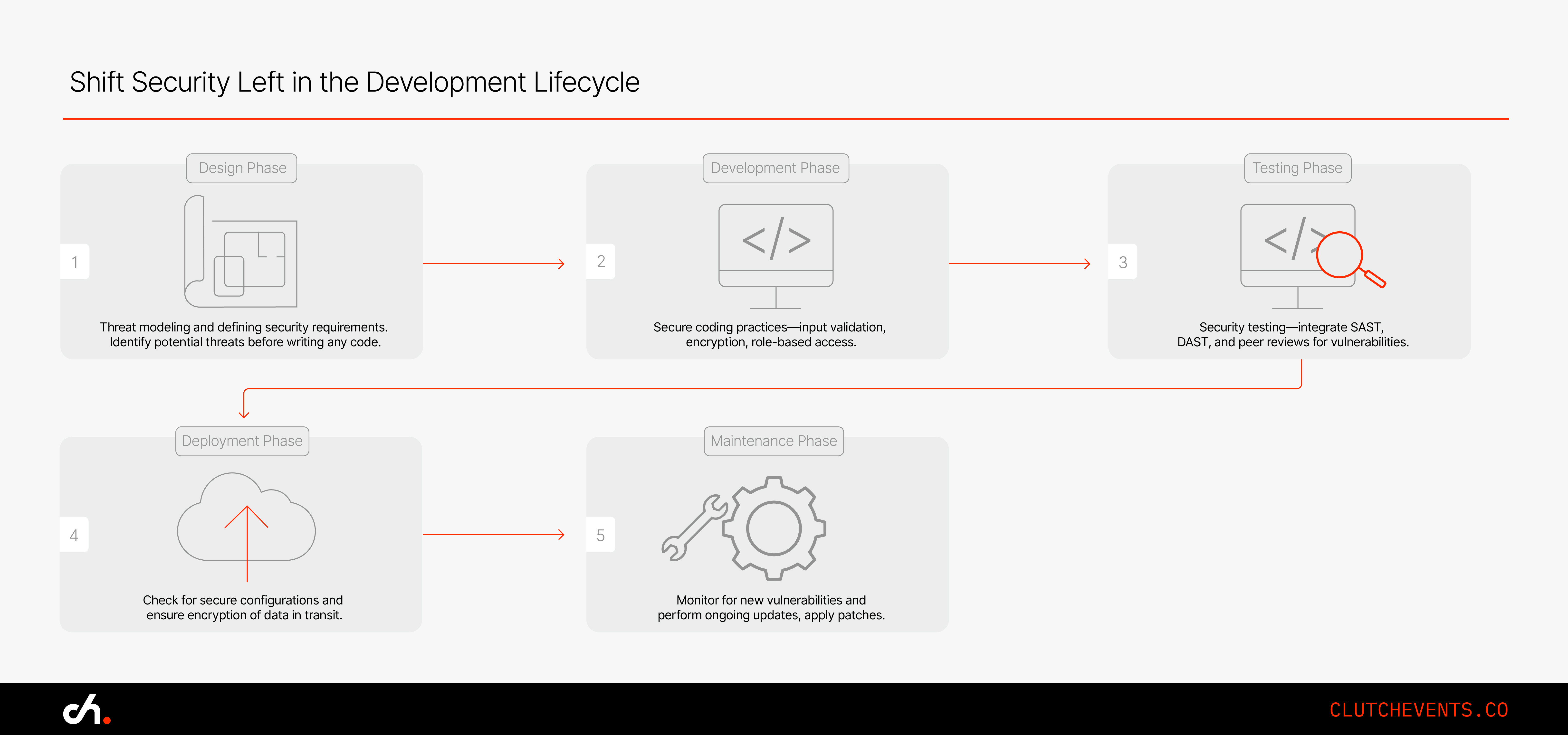
1. Bring Security Into the Development Lifecycle from Day One
If you’ve ever hit a security snag just before launch, you’re not alone. That’s the trap of waiting too long to think about threats. Shifting security to the beginning of the development cycle saves time and reduces friction. It’s a preventative mindset, not a reactive scramble.
So what does "shifting left" really mean?
It means security work begins the moment planning starts. You don’t wait for QA to flag a security issue after months of work. You start by identifying the risks in your design and building defenses into the foundation.
What you can do:
- Start with threat modeling. As soon as you start architecting a feature, ask the tough questions. What’s the worst someone could do with this? Could it expose user data? What if an attacker gained access to this endpoint?
- Define security requirements like you would product features. If you’re collecting payment data, specify what encryption standards you’ll use. If users need access control, determine how roles will be structured. This clarity early on helps guide development and avoid messy patches later.
- Use peer reviews that focus on security. Don’t wait until QA to care. Regular, lightweight reviews with a security lens help teams catch mistakes early and they’re fast once it becomes habit.
Thinking about security this early reduces how many bugs make it into production. That means fewer headaches down the line, fewer missed deadlines, and fewer costly reworks.
2. Code Defensively…. It’s Not Just for Pen Testers
Secure coding practices aren’t optional anymore. From SQL injections to cross-site scripting, the same old vulnerabilities still show up in production apps today. Why? Because input validation and authentication are often skipped or rushed.
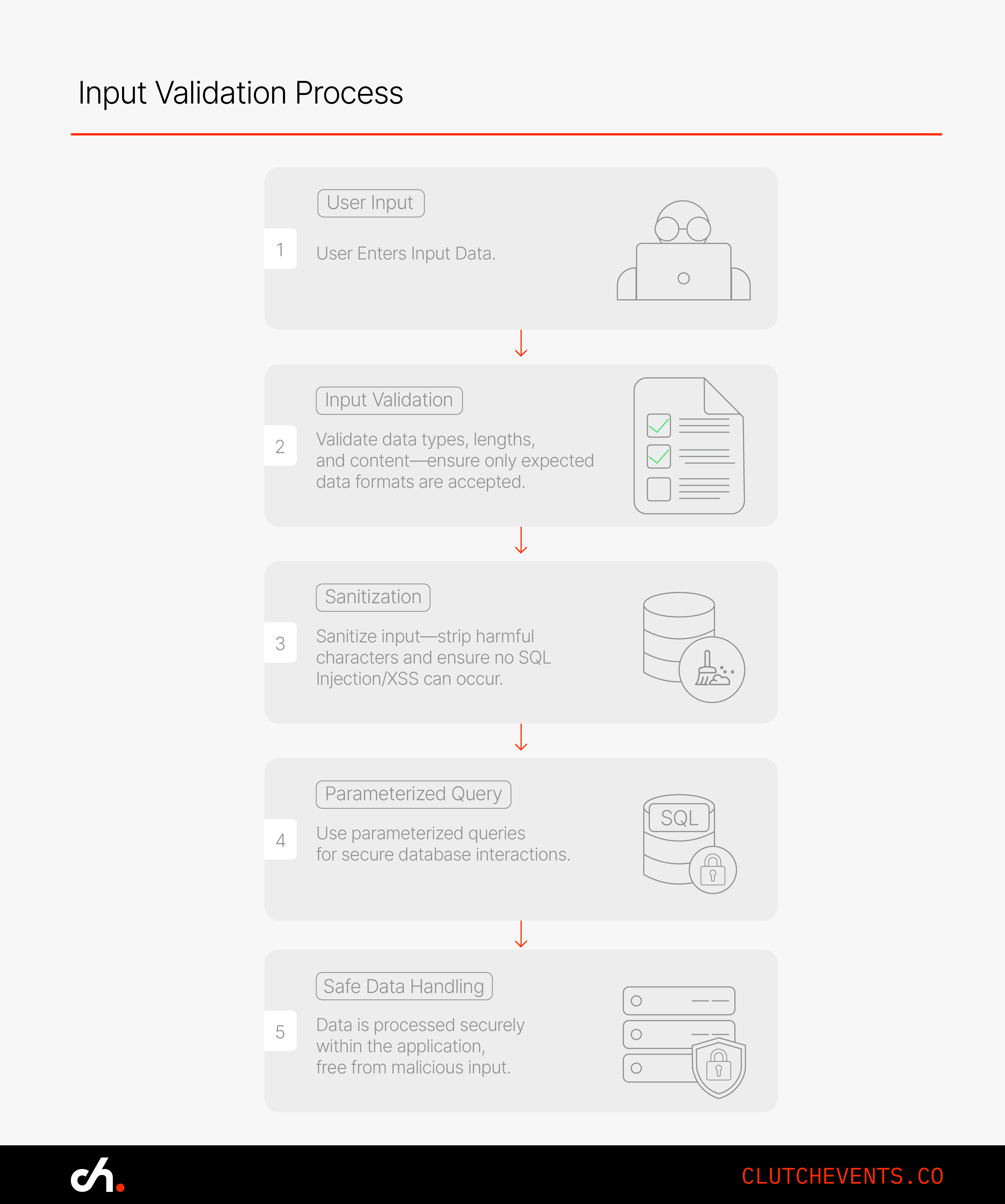
2.1 Input Validation: Your App’s Front-Line Defense
You wouldn’t run an event without a guest list. Don’t run an app without validating input. Attackers don’t need admin credentials when they can just sneak bad data through your front door.
Start by:
- Sanitising input. Scrub it. Escape characters. Assume nothing. If it’s going into a database, use parameterised queries. Preventing injection is as basic as locking your door at night.
- Enforcing data types and lengths. Expect a phone number? Accept only digits. Getting an email address? Use a pattern match. The more you constrain what gets in, the safer your app becomes.
2.2 Authentication and Authorization: Keep the Right People in the Right Places
Anyone with a password shouldn’t be able to access everything. That’s just asking for trouble. Strong authentication and granular access control are essential.
- Use multi-factor authentication. Passwords alone are weak. A second factor, something users have, like a device, makes attacks significantly harder.
- Implement role-based access control (RBAC). Give people and services only the access they need. If someone’s job doesn’t involve financial data, they shouldn’t be able to see it.
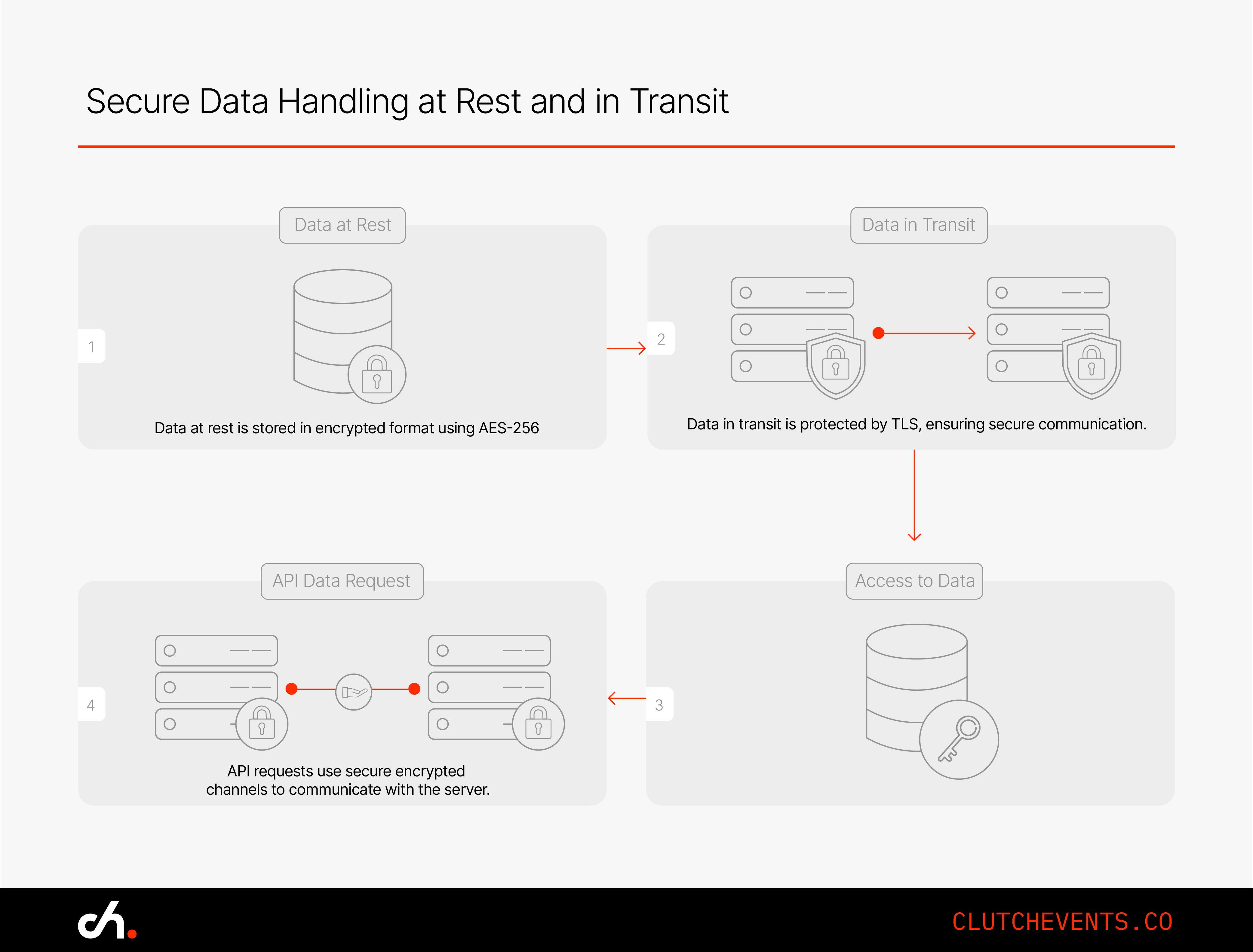
2.3 Protect Data Everywhere It Lives or Moves
If you’re storing sensitive data unencrypted, you’re effectively leaving it on your desk with the office door open.
- Encrypt at rest and in transit. Stick to AES-256 for stored data and TLS for anything moving over the network. This is table stakes.
- Keep secrets out of your codebase. No hardcoded API keys. No passwords in config files. Use environment variables or dedicated secret management tools instead.
3. Use Security Tools That Catch Problems Before They Spread
There’s no reason to rely only on human vigilance. Plenty of tools now catch common issues in seconds.
3.1 Static Application Security Testing (SAST)
SAST tools scan your source code as you write it. Think of it like linting, but for vulnerabilities. They’re useful during coding and CI builds.
- Try Snyk or SonarQube. Both integrate easily into developer workflows and flag problems early, while your code is still taking shape.
3.2 Dynamic Application Security Testing (DAST)
Where SAST looks at your code, DAST behaves like an attacker hitting your app. It finds misconfigurations, unprotected endpoints, and real-world weaknesses.
- Run OWASP ZAP or Burp Suite regularly. These tools simulate live attacks and show what an attacker could see or exploit once your app is running.
3.3 Dependency Scanning
Most modern codebases rely heavily on libraries. If one of them is compromised, your app is too.
- Automate updates with Dependabot. It monitors for vulnerabilities in packages and nudges you when updates are available. Staying current reduces your risk surface significantly.
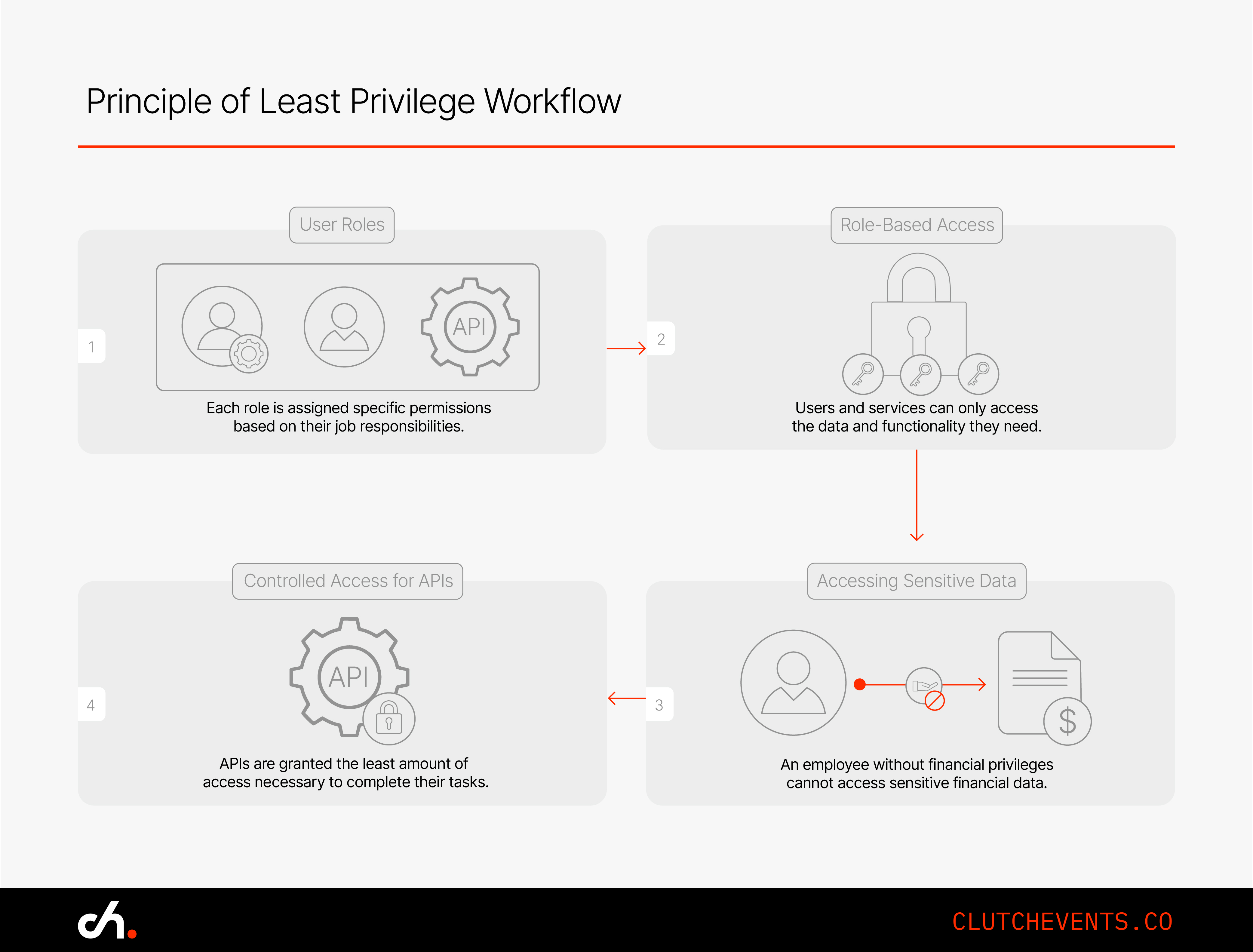
4. Apply the Principle of Least Privilege
Security is often about minimizing damage when things go wrong. The Principle of Least Privilege (PoLP) ensures that users, services, and processes only have access to what they absolutely need…no more.
4.1 Limit Access Wherever You Can
- Don’t mix data unnecessarily. A reporting tool doesn’t need write access to HR data. The fewer places a breach can reach, the better.
- Be strict with service permissions. A read-only database user should not have write access. Cloud services should have tightly scoped roles. If a service is compromised, limited permissions can save you from a full-scale incident.
It’s like giving someone a key to the front door, not every room in the house.
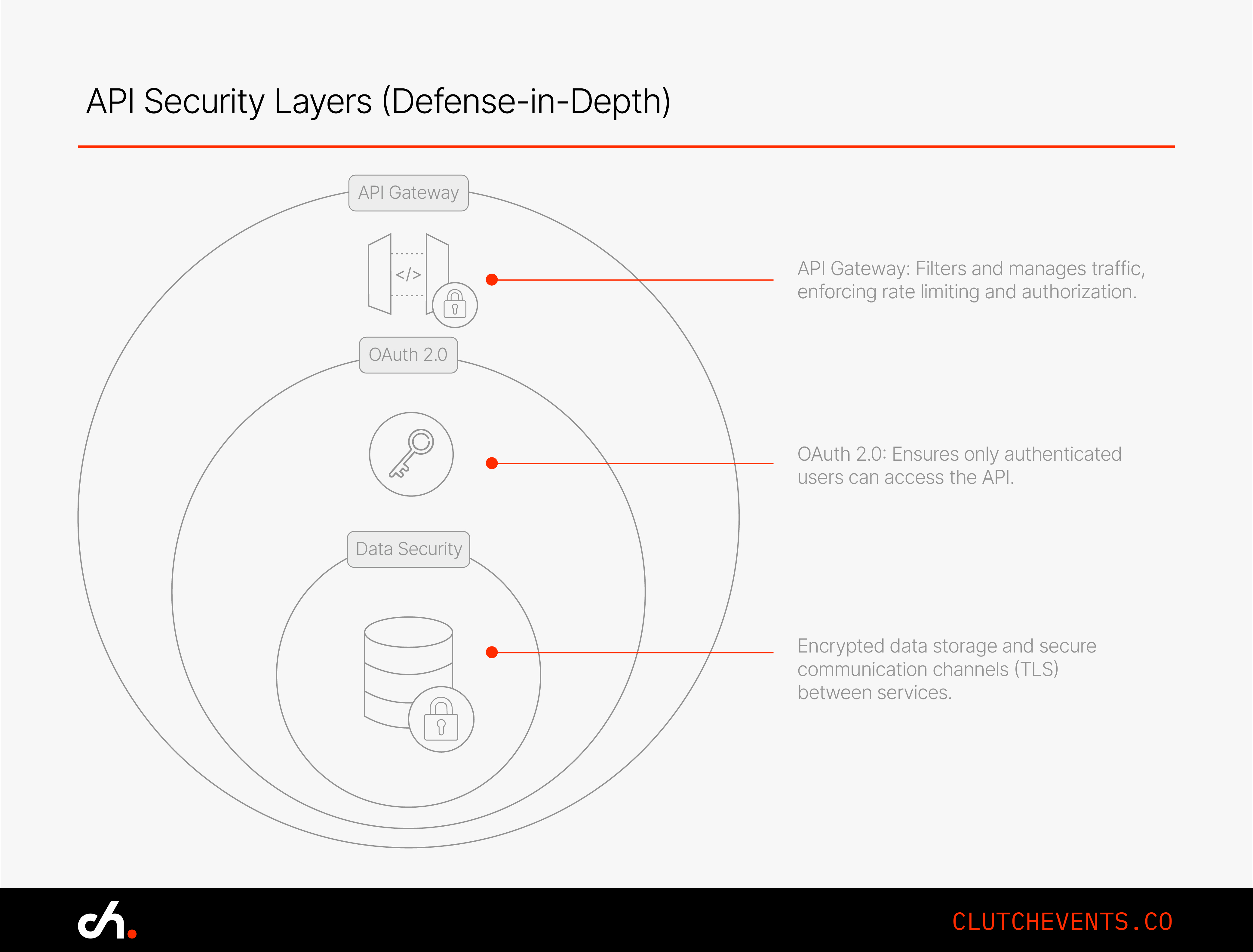
5. Lock Down APIs and Microservices
Microservices make apps modular and scalable, but they also create more doors for attackers. If your services are exposed without proper protection, that’s a security incident waiting to happen.
5.1 Use OAuth 2.0
Let services prove who they are with tokens, not passwords. OAuth gives granular access that expires when it should. It’s cleaner, safer, and industry standard.
5.2 Rate-Limit and Throttle
If someone starts hammering your API, you need to be ready. Without rate limiting, a simple misbehaving client or a malicious actor can bring your backend down fast.
Use API gateways to enforce limits and block abuse early.
6. Build Privacy In, Not Around
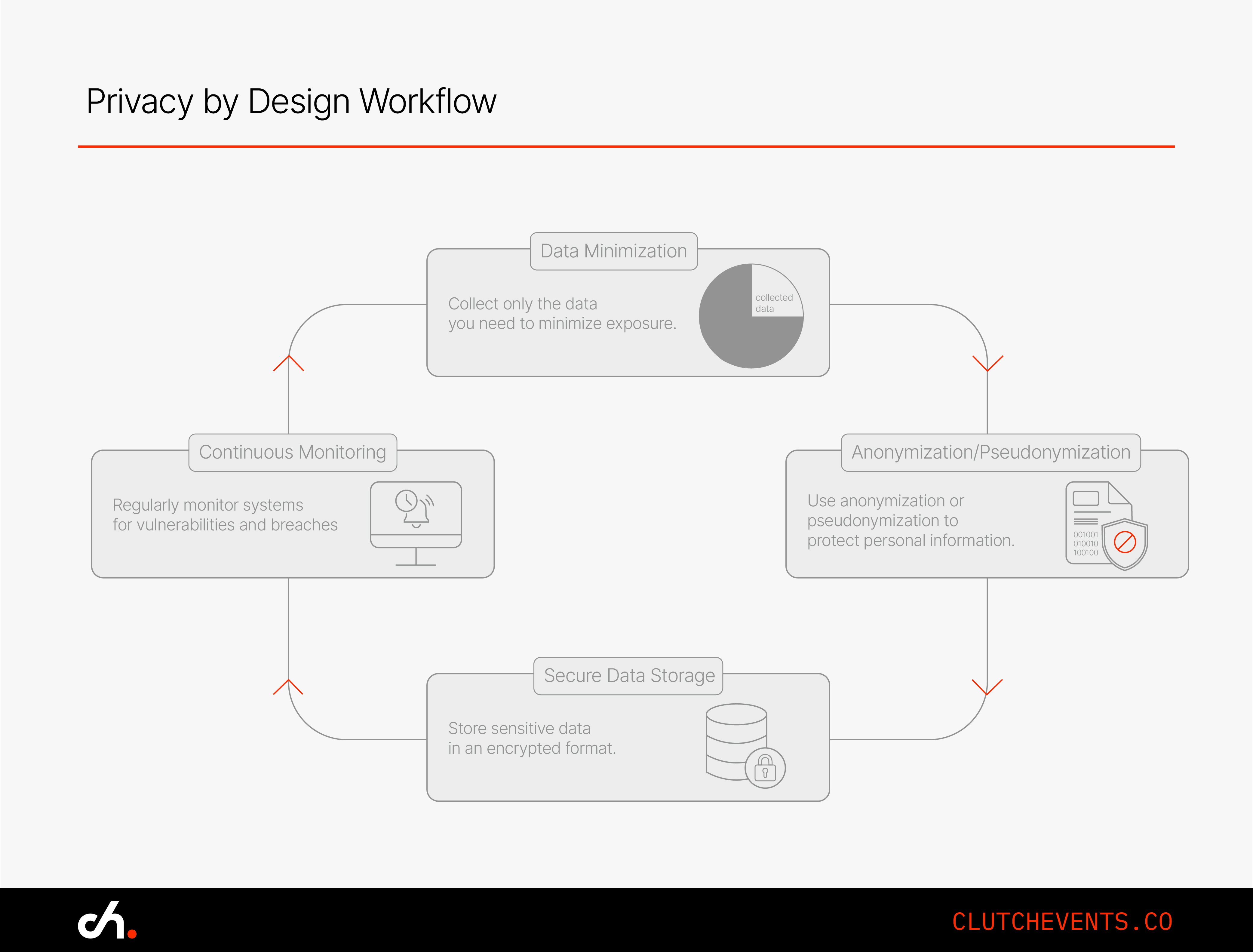
Security without privacy is incomplete. Regulations like GDPR and CCPA have forced companies to rethink how they handle data. Smart teams aren’t just reacting to fines, they’re designing with privacy in mind from the start.
6.1 Collect Less, Store Smarter
Only gather the data you truly need. Every extra field is an extra liability. Ask yourself: do we really need to store this? And if the answer is yes, make sure it's encrypted and access-controlled.
6.2 Use Anonymization and Pseudonymization
If personal data isn’t essential, strip it out. Or mask it. That way, even if data is leaked, it’s much harder to trace back to a person. This isn’t just good practice. It’s often required by law.
7. Make Security Part of the Culture
You can have the best tools and policies in the world, but if your team doesn’t care about security, none of it matters. A security-first culture comes from continuous learning and shared responsibility.
7.1 Train Continuously
Offer regular training…not once a year, but as part of the development cycle. Platforms like OWASP, Secure Code Warrior, and Coursera are great starting points.
7.2 Break Down Silos
Security shouldn’t sit only with one team. Developers, operations, and security engineers should regularly collaborate. Share wins, flag risks, and learn together.
Conclusion: Build Secure, Build Smart
In a world where data leaks can cost millions and trust is hard to win back, building security into your code isn’t optional. It’s essential. By applying the principles in this guide, you’ll build software that’s not just functional and fast but resilient, trusted, and future-proof.
Start small. Add one layer at a time. Use the tools available. Train your team. Then keep going. Because the stakes aren’t just technical anymore, they’re business-critical.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand


