Crafting User-Specific Conditional Access Policies: Managing Hybrid Workforces with Granular Controls

Introduction
The hybrid work model has fundamentally reshaped the landscape of identity and access management (IAM). With employees accessing corporate resources from a range of locations and devices, managing access securely has become a complex challenge. Traditional access control methods, which often operate with binary “allow” or “deny” logic, fall short in addressing the diverse, context-specific needs of today’s workforce.
Conditional access policies - access decisions based on dynamic conditions, such as user role, location, device health, and behaviour - offer a robust solution to this complexity. However, crafting user-specific conditional access policies that remain flexible, scalable, and secure across a hybrid workforce requires a strategic approach.
This technical deep dive explores how to implement user-specific conditional access policies effectively, including best practices, potential challenges, and the tools that make this possible.
The Role of Conditional Access in Hybrid Work Environments
Conditional access provides a more sophisticated way to control access to resources by evaluating the context of each access attempt. While traditional access control methods grant or deny access based purely on a user’s identity or role, conditional access introduces additional layers of security by analysing situational factors, allowing more adaptive and granular permissions.
Core Components of Conditional Access:
- Identity-Based Conditions: Access decisions based on user identity, such as role, group membership, or department.
- Device-Based Conditions: Criteria include device health status, type, and ownership (corporate vs. personal).
- Location-Based Conditions: Access is restricted or permitted based on geographic location or trusted networks.
- Behavioural-Based Conditions: Analyses recent user behaviour to detect anomalies and respond dynamically.
Example in Practice: A hybrid workforce member working from a home network might access internal resources with minimal friction, but accessing the same resources from an unrecognised location would trigger additional verification requirements, such as multi-factor authentication (MFA).
Conditional access has become essential for hybrid work environments by enabling organisations to tailor policies based on specific, contextual criteria that protect resources without sacrificing user convenience.
Challenges of Managing Access for Hybrid Workforces
Managing access for a distributed, hybrid workforce introduces several unique challenges:.
- Diverse Device Types and States
- Hybrid workers often use a mix of corporate and personal devices, each with different security standards. Ensuring secure access from varying device types without imposing overly restrictive measures on users requires granular device-based policies.
- Dynamic Access Requirements
- Access needs for hybrid employees change frequently based on their location, tasks, or even the time of day. Conditional policies must dynamically adapt to these shifting requirements without extensive administrative overhead.
- Data Privacy and Regulatory Compliance
- Managing conditional access for a hybrid workforce often means dealing with varying compliance requirements (e.g., GDPR, HIPAA). Policies need to account for these regulations by restricting access based on user location and data sensitivity, which adds complexity.
- Risk of Over-Complexity
- The more granular an access policy, the harder it can be to manage effectively. Excessively complex policies can introduce security risks, increase administrative burden, and reduce policy effectiveness if they are not regularly reviewed and optimised.
Real-World Tip: Balance between granular policies and administrative simplicity by starting with broad conditional policies and refining them based on usage insights and risk assessments.
Key Takeaway: A successful conditional access strategy in a hybrid workforce hinges on balancing security with user convenience and administrative efficiency.
Key Strategies for Crafting User-Specific Conditional Access Policies
Crafting user-specific conditional access policies requires a multi-layered approach to balance security needs with ease of access. Here are the core strategies:
1. Identity-Based Policy Customisation
Identity-based policies ensure that users can access resources based on their role, department, or specific responsibilities. This approach allows for policies that are tailored specifically to groups or individual users, ensuring that they have access to the resources they need without compromising security.
- Example: Finance department employees are granted access to financial databases only within business hours, while IT administrators have continuous access for maintenance tasks.
- Implementation Tip: Use tools that support role-based access control (RBAC) to define initial user permissions, and layer additional identity-based conditions as needed.
Quick Takeaway: To streamline management, start with broad roles and refine with specific conditions, ensuring a balance between security and ease of access.
2. Device-Based Conditional Policies
Device-based policies assess the security posture of the device attempting access. These policies enforce restrictions or additional requirements based on factors such as whether the device is corporate-owned or personal, its operating system, and the device’s compliance with security standards (e.g., updated antivirus software or encryption).
Think of it this way: Devices are like different doors to your organisation, and each door requires a unique key depending on its security status.
- Example: A corporate device with full security patches may access sensitive resources without restrictions, while a personal device accessing the same resource must pass additional security checks.
- Real-World Tip: For organisations with both corporate-owned and bring-your-own-device (BYOD) models, consider creating separate policy categories. Corporate devices may pass through with fewer restrictions, while BYOD devices can trigger additional verification steps.
Quick Takeaway: For a hybrid workforce, create device policies that are flexible enough to accommodate personal device use while maintaining a strict security posture for sensitive data.
3. Location-Based Access Control
Location-based controls add a valuable layer of security by allowing or restricting access based on geographic or network location. This approach reduces risk by identifying and restricting access from unknown or high-risk locations.
- Example: A remote employee’s login attempt from a trusted location (e.g., their home) could have minimal restrictions, while an attempt from a foreign country might trigger multi-factor authentication.
- Implementation Tip: Use geo-fencing techniques to restrict access to specific resources based on trusted IP ranges or known safe locations.
Quick Takeaway: Establish trusted locations and IP ranges to streamline access for regular locations while adding more robust checks for unfamiliar access attempts.
4. Risk-Based Access with Behavioral Analytics
Behavioural analytics monitor user actions over time to establish a baseline of normal activity and identify unusual patterns. When a user’s behaviour deviates from this baseline, risk-based access control can step in to restrict or verify access, providing a dynamic, user-specific approach to security.
In other words: Baselines help define what ‘normal’ looks like, so anything unusual can be flagged for further review.
- Example: A user with a history of accessing data from a specific network might face additional checks if they suddenly attempt access from a different country.
- Real-World Tip: Start by implementing baseline behavioural tracking to establish what “normal” looks like for different roles, then adjust risk tolerance based on access sensitivity.
Quick Takeaway: Behavioural tracking works best when applied to high-risk roles, like administrators, where deviations are more likely to indicate a risk.
Analogy: Think of risk-based access as a thermostat that adjusts the temperature automatically based on the surrounding conditions. It adapts security requirements depending on the user’s context, responding to changes in access patterns as they arise.
Tools for Implementing User-Specific Conditional Access Policies
Several tools enable organisations to implement and manage conditional access policies effectively, with options that vary based on specific needs and existing infrastructure. Here’s a look at key tools for enforcing user-specific access in hybrid environments:
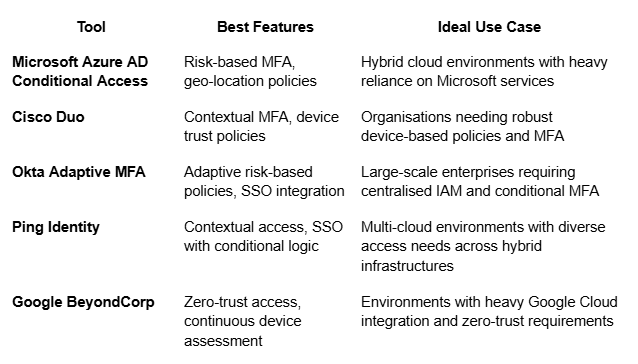
Best Practices for Managing Conditional Access Policies
Implementing conditional access policies is only the first step; to be effective, these policies need regular monitoring, updating, and optimisation. Here are some best practices for managing user-specific conditional access policies:
1. Establish Clear Baselines and Monitor Usage
Monitoring and understanding user behaviour is critical to creating effective conditional policies. Start by setting baselines for normal activity across different roles and departments, then continuously track policy effectiveness and adjust as needed.
- Actionable Tip: Use data collected from access logs to refine conditional policies and identify new criteria for adaptive controls.
2. Enforce the Principle of Least Privilege
The principle of least privilege ensures users have only the permissions necessary to perform their tasks. This principle not only minimises security risks but also reduces policy complexity by limiting access needs.
- Real-World Tip: Regularly audit access permissions and remove outdated permissions or policies no longer in use.
3. Implement Multi-Factor Authentication (MFA) for High-Risk Access
MFA provides a critical layer of security for high-risk activities, particularly those involving sensitive resources or access attempts from untrusted networks.
- Actionable Tip: Apply risk-based MFA policies that require additional verification based on conditions like location or device health, rather than universally across all access attempts.
4. Regularly Review and Update Policies
Conditional access policies need to evolve with changing security requirements and user behaviour patterns. Regular reviews ensure policies remain effective and up-to-date with emerging threats.
- Quick Takeaway: Schedule quarterly policy reviews, incorporating insights from incident reports and access logs to update criteria and adapt to evolving hybrid workforce needs.
5. Ensure Transparency and Communication with Users
User awareness is critical to the success of any conditional access policy. Informing users about security practices and conditions that may impact their access can improve cooperation and reduce friction in access processes.
- Real-World Tip: Share guidelines on how location, device security, and access behaviour may impact their permissions to promote understanding and compliance.
Key Takeaway: Effective management of conditional access policies involves ongoing refinement, regular audits, and clear communication with users, ensuring both security and productivity are maintained.
Real-World Applications of User-Specific Conditional Access Policies
Conditional access policies are widely applied across industries to protect sensitive data and ensure compliance with regulations. Here are two examples of industry-specific applications:
- Financial Services: Banks and financial institutions leverage conditional access policies to protect client data and meet regulatory requirements. Finance employees, for example, may have conditional access to client information based on their physical location, device security posture, and specific roles. Access to financial records is further limited during non-business hours to reduce exposure.
- Healthcare: Healthcare providers use conditional access to protect patient data and ensure compliance with HIPAA. Policies often require doctors and nurses to authenticate with additional factors when accessing sensitive patient records from mobile devices. Role-based policies restrict access to certain patient information based on department and job function, while device-based policies verify that only compliant devices are used for accessing patient data.
Added Industry Examples:
- Education Sector: In higher education, conditional access can restrict administrative access to sensitive student records to specific campus locations or approved networks.
- Retail and E-commerce: Retailers can implement device-based conditional access to ensure only verified devices handle payment processing, securing transaction data across devices and locations.
Conclusion
Crafting user-specific conditional access policies is crucial for managing the security demands of a hybrid workforce. By implementing policies based on identity, device, location, and behaviour, organisations can achieve a flexible, adaptive approach that balances security and convenience.
Using tools that support conditional access, enforcing best practices like least privilege and regular audits, and understanding the unique requirements of your workforce are all key steps in securing resources effectively.
In today’s hybrid world, the ability to dynamically adapt to changing access needs isn’t just an option; it’s a necessity for securing sensitive information and maintaining business continuity.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand



