Enforcing Attribute-Based Policies in Multi-Tenant Kubernetes Clusters: Securing User Access in Shared Environments

Introduction
Imagine running a bustling hotel where each guest has a unique itinerary. Some have access to the gym, others to the spa, and a few VIPs can access the executive lounge. Now picture managing all this without room keys or access badges. Chaos, right? This is what an unmanaged multi-tenant Kubernetes cluster looks like: shared infrastructure without clearly defined access boundaries.
Kubernetes has become the backbone of modern containerised applications, but as organisations scale, multi-tenancy introduces new challenges. Each tenant whether a team, application, or organisation requires secure isolation to prevent unauthorised access and data leaks. Managing user access in such an environment is no small feat, especially when tenants demand flexibility and compliance with stringent security standards.
Traditionally, Kubernetes relies on Role-Based Access Control (RBAC) to manage permissions. But RBAC, while useful, has limitations in dynamic and complex environments. Enter Attribute-Based Access Control (ABAC): a flexible, fine-grained solution that considers multiple attributes user roles, resource metadata, and contextual factors to dynamically decide access.
This article explores how ABAC works, why it’s critical for securing multi-tenant Kubernetes clusters, and how to implement it effectively. From practical examples to scalability strategies, we’ll cover everything you need to know to secure shared environments.
What Makes ABAC the Secret Sauce for Kubernetes Security?
The Challenge of Multi-Tenant Kubernetes Clusters
Imagine Kubernetes as a bustling city. Namespaces act as neighborhoods, pods are buildings, and tenants are residents. A multi-tenant cluster is like a shared city where different teams or organisations must coexist securely. However, this shared environment creates challenges:
- Resource Isolation: Tenant A’s resources should be invisible to Tenant B.
- Dynamic Workloads: Tenants may deploy, scale, or delete workloads unpredictably.
- Compliance: Regulatory frameworks like SOC 2, HIPAA, or GDPR demand strict access controls and audit logs.
- Scalability: Policies must scale with clusters containing thousands of users and resources.
When these challenges aren’t addressed, you’re left with overlapping permissions and vulnerable systems.
Why RBAC Alone Isn’t Enough
RBAC is like giving out pre-labeled keys at a hotel: a key for the gym, another for the spa, and so on. While efficient for static access patterns, RBAC struggles in dynamic environments. It can’t account for context, like allowing gym access only during off-peak hours or denying access based on user location.
RBAC’s Limitations in Kubernetes:
- Static and role-centric, RBAC can’t handle:
- Dynamic user attributes like department or project.
- Resource metadata such as labels or annotations.
- Environmental conditions like time, IP address, or device type.
Enter ABAC:
Unlike RBAC, ABAC evaluates access dynamically based on attributes. Instead of simply asking, “What’s your role?” it asks, “What’s your role, which resource are you trying to access, and what’s the context?”
RBAC vs. ABAC: The Hybrid Solution
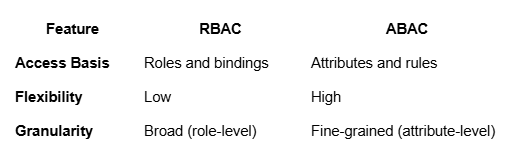
For hybrid setups:
- Use RBAC for broad role-based permissions.
- Add ABAC for dynamic, fine-grained access control.
Scaling ABAC Without Losing Your Sanity
How ABAC Works
At its core, ABAC evaluates attributes associated with:
- Users: Identity attributes like department, role, or group membership.
- Resources: Labels, namespaces, or annotations describing the resource.
- Environment: Contextual metadata, such as access time or IP address.
Policies define how these attributes interact to determine whether access is granted. For example:
- A user in the “finance” department can only access resources labeled “finance” during business hours.
Core Components of ABAC
- Attributes: Metadata defining users, resources, and context.
- Policy Engine: The logic (e.g., Open Policy Agent) that evaluates access requests.
- Enforcement Point: Kubernetes Admission Controllers enforce decisions from the policy engine.
Analogy: Think of the policy engine as a restaurant host verifying a reservation. Instead of just checking a name, they also confirm the time and table details to ensure you’re allowed entry.
Implementing ABAC in Kubernetes: What’s Under the Hood?
Step 1: Defining Attributes
Attributes are the foundation of ABAC. In Kubernetes, these attributes can include:
- User Metadata: Identity provider details like Azure AD or Okta, including group or department.
- Resource Metadata: Labels or annotations (e.g., “team: backend”).
- Environment Metadata: Variables like IP address, time of access, or device type.
Example Use Case:
A policy might state: “Only developers in the ‘backend’ team can create pods labeled ‘test’ in the ‘staging’ namespace.”
Step 2: Setting Up Open Policy Agent (OPA)
Why OPA?
OPA acts as the policy engine for Kubernetes. It intercepts API requests, evaluates them against defined policies, and returns a decision to the Admission Controller.
Steps to Integrate OPA:
- Deploy OPA as a sidecar or standalone pod.
- Write policies using OPA’s Rego language.
- Configure Kubernetes Admission Controllers to forward API requests to OPA.
- Validate policies in a staging environment before rolling them out cluster-wide.
Rego Policy Example:
rego
Copy code
package kubernetes.authz
default allow = false
allow {
input.user.department == "finance"
input.resource.labels["team"] == "finance"
input.namespace == "finance-namespace"
}
Performance Considerations:
- Real-time policy evaluation introduces slight latency.
- To minimise this, optimise Rego policies and consider caching frequently evaluated results.
Step 3: Monitoring and Auditing
Visibility is essential for secure multi-tenancy. Tools like Kubernetes Audit Logs and OPA’s built-in logging help track:
- Policy evaluations.
- Unauthorised access attempts.
- Compliance violations.
Example Audit Log Entry:
json
Copy code
{
"user": "john.doe",
"attributes": {
"department": "finance",
"action": "create",
"resource": "pod"
},
"decision": "allowed"
}
Addressing Scalability Challenges in Massive Clusters
Managing ABAC in small clusters is straightforward, but scaling to thousands of tenants introduces new complexities.
Key Scalability Challenges:
- Policy Evaluation Overhead: High request volumes require policies to process dynamically, introducing latency.
- Management Complexity: Maintaining attribute definitions and policies across tenants can become cumbersome.
- Resource Contention: Shared control plane resources may struggle under the load of frequent evaluations.
Strategies to Mitigate Scalability Issues
- Optimise Policy Evaluation:
- Reduce nested conditions and leverage caching mechanisms.
- Group and Hierarchise Policies:
- Group policies by namespace or tenant to reduce evaluation scope.
- Distribute Policy Evaluation:
- Run OPA instances in a distributed setup to balance the load.
- Proactive Monitoring and Scaling:
- Monitor latency metrics and scale OPA instances dynamically.
Real-World Example
A SaaS provider with 10,000 tenants implemented ABAC using OPA. Initially, they experienced latency due to complex policies. By grouping policies by namespace and caching frequent evaluations, they reduced response times by 50%.
Rhetorical Question:
As your clusters grow, are your ABAC policies designed to scale?
Future Trends in Kubernetes Access Control
Decentralised Identity
Projects like Microsoft’s decentralized identity aim to let users control authentication data, paving the way for secure, tenant-controlled Kubernetes environments.
Post-Quantum Cryptography
NIST’s quantum-resistant cryptography standards could protect ABAC systems against emerging quantum threats.
Conclusion
Securing multi-tenant Kubernetes clusters requires dynamic solutions like ABAC. By combining flexibility with fine-grained control, ABAC ensures secure, scalable environments.
The question is, are your access policies ready for the demands of tomorrow?
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand



