Implementing Attribute-Based Access Control in Kubernetes: A Practical Guide for Dynamic Environments

Introduction
Imagine being a manager of a bustling coworking space where clients from startups to enterprises share the same building. Each team needs access to specific areas, such as meeting rooms or high-security storage. Some need round-the-clock access; others only during work hours. Now imagine handing out a single generic key to everyone what could go wrong? This chaos is what happens when Kubernetes clusters lack fine-grained access control
Kubernetes is the backbone of modern application deployments, but managing access in its dynamic, shared environments remains a challenge. Traditional Role-Based Access Control (RBAC) models work well in static setups but often fall short in highly dynamic, multi-tenant clusters where permissions depend on a mix of user roles, resource metadata, and real-time environmental factors.
This is where Attribute-Based Access Control (ABAC) shines. ABAC evaluates access dynamically based on attributes, enabling fine-grained control for dynamic workloads. In this guide, we’ll explore ABAC’s concepts, delve into its implementation in Kubernetes using Open Policy Agent (OPA), and discuss performance, scalability, and best practices. Along the way, we’ll sprinkle in real-world examples, humor, and actionable insights to ensure you’re fully equipped to tackle your Kubernetes access challenges.
What Is Attribute-Based Access Control?
Defining ABAC
Attribute-Based Access Control (ABAC) is a policy-based framework that determines access based on a combination of attributes:
- User Attributes: Information about the user (e.g., department, role, project).
- Resource Attributes: Metadata tied to the resource (e.g., labels, annotations).
- Environment Attributes: Contextual factors like time, IP address, or device.
Unlike RBAC, which assigns permissions solely by roles, ABAC adds context to the decision-making process.
ABAC vs. RBAC
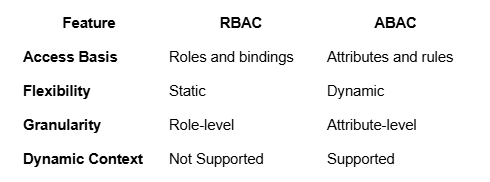
Analogy: Think of RBAC as a "club membership" where you either have access or you don’t. ABAC, however, is like a guest list for an exclusive event: it checks not only your name but also your reservation time, dress code, and whether you’re on the VIP list.
Why ABAC Matters in Kubernetes
Kubernetes’ dynamic nature demands more than static role-based permissions. Imagine this scenario:
- Developers need access to testing environments during office hours.
- Finance teams should only access billing-related pods within a specific namespace.
- Certain resources should only be accessible from a secure corporate network.
RBAC struggles to handle these dynamic requirements, but ABAC thrives in such setups by dynamically evaluating policies based on multiple attributes.
How Kubernetes Handles Access Control
Default Mechanisms
Kubernetes provides built-in access controls:
- RBAC: Assigns static roles and bindings.
- Network Policies: Manages pod-to-pod communication.
- Pod Security Admission: Enforces pod-level restrictions.
While effective in static environments, these tools lack the flexibility to handle multi-dimensional access requirements.
Implementing ABAC in Kubernetes: A Step-by-Step Guide
Step 1: Define Attributes
Attributes are the core of ABAC. Kubernetes uses:
- User Metadata: Roles, groups, and departments from identity providers (e.g., Azure AD, Okta).
- Resource Metadata: Labels, annotations, and namespaces in Kubernetes.
- Environment Metadata: Contextual data like time of access or IP address.
Step 2: Set Up Open Policy Agent (OPA)
Why OPA?
OPA is like the "gatekeeper" of Kubernetes. It intercepts API requests, evaluates policies, and decides whether to allow or deny the request.
How to Integrate OPA:
- Deploy OPA as a pod or sidecar.
- Write policies using OPA’s Rego language.
- Configure Kubernetes Admission Controllers to forward API requests to OPA.
- Validate policies in a staging environment.
Example Rego Policy:
rego
Copy code
package kubernetes.authz
default allow = false
allow {
input.user.department == "dev"
input.resource.labels["team"] == "dev-team"
input.namespace == "staging"
}
Step 3: Test Policies
Testing ensures your policies work as expected. Use realistic workloads and monitor for:
- Misconfigured permissions.
- Performance bottlenecks during evaluation.
Pro Tip: Automate policy testing using CI/CD pipelines to simulate attribute updates dynamically.
Performance and Scalability Considerations
Latency Metrics
Real-time policy evaluation adds slight latency (~5–10ms per request). While negligible for small clusters, this becomes critical at scale.
Mitigation Strategies
- Optimise Rego Policies: Avoid deeply nested conditions.
- Implement Caching: Cache frequent evaluations to reduce overhead.
Distribute OPA Instances: Use multiple replicas to balance the load.
Handling Edge Cases
- Overlapping Attributes: Use priority rules to resolve conflicts between policies.
- Dynamic Updates: Ensure attribute updates (e.g., team changes) are synchronized in real time via identity providers.
Best Practices for Dynamic Environments
- Combine ABAC with RBAC: Use RBAC for broad roles, with ABAC for granular controls.
- Automate Attribute Updates: Sync user attributes with identity providers like Azure AD.
- Audit Regularly: Periodically review logs for policy violations or misconfigurations.
- Centralise Policy Management: Store policies in a version-controlled repository for consistency.
Example: Automate namespace isolation by integrating OPA with GitOps workflows.
Next Steps
- Evaluate Your Current Model:
- Are static roles limiting your access control flexibility?
- Deploy OPA in a Test Cluster:
- Start with basic Rego policies and gradually expand.
- Monitor and Iterate:
- Use tools like Prometheus to monitor policy evaluation times.
- Explore Future Trends:
- Investigate decentralised identity systems for long-term adaptability.
Future Trends in Kubernetes Access Control
- Decentralised Identity:
Projects like Microsoft’s decentralised identity system use blockchain for user-controlled authentication. - Post-Quantum Cryptography:
As quantum computing advances, NIST-approved algorithms will secure ABAC policies against quantum attacks. - AI-Driven Policy Automation:
Machine learning can analyze access patterns to recommend or generate policies, reducing manual overhead.
Conclusion
Attribute-Based Access Control (ABAC) is the ideal solution for managing dynamic Kubernetes environments. By leveraging OPA and aligning policies with real-world attributes, ABAC enables precise, flexible, and scalable access control. Whether you’re securing a small cluster or a multi-tenant ecosystem, ABAC equips you to meet today’s challenges while preparing for tomorrow’s innovations.
Are your Kubernetes policies ready for the future of access control? The time to act is now.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand



