Ghost Resources in the Cloud: Finding and Eliminating Abandoned Assets Across Multi-Cloud Environments

Ghost resources, also known as zombie assets, are cloud components that are no longer in use but remain active, consuming budget and increasing your attack surface. In multi-cloud environments, these are hard to track, easy to ignore, and dangerous if exploited.
This deep dive covers practical techniques to detect and remove abandoned assets in AWS, Azure, and GCP. It also outlines tagging, alerting, and policy strategies to keep your environment clean.
What Counts as a Ghost Resource?
- Detached storage volumes (e.g., EBS, Azure Managed Disks, GCP Persistent Disks)
- Unattached IPs or load balancers
- Old machine images and snapshots
- Unused IAM roles, keys, and service accounts
- Orphaned cloud functions or Lambda handlers
- Abandoned containers or Kubernetes namespaces
These resources may not appear in usage dashboards, but they:
- Cost money
- Increase your attack surface
- Complicate inventory and compliance
Discovery Techniques by Cloud Provider
AWS
- Use AWS Config to track resource changes and drift.
- Query unused EBS volumes:
(Put in code box) aws ec2 describe-volumes --filters Name=status,Values=available
- Identify unused security groups:
(Put in Code box) aws ec2 describe-security-groups | jq '.SecurityGroups[] | select(.IpPermissions == [] and .IpPermissionsEgress == [])'
- Use Trusted Advisor and Resource Explorer to scan for idle assets.
Azure
- Use Azure Resource Graph Explorer to query for detached disks:
(Put in code box) Resources
| where type =~ 'microsoft.compute/disks'
| where properties.diskState == 'Unattached'
- Run Azure Advisor for recommendations on underutilised assets.
- Use Azure Policy to enforce lifecycle tagging and expiration.
GCP
- Use Asset Inventory with gcloud:
(put in code box) gcloud asset search-all-resources --query='state=UNUSED' --scope=projects/your-project-id
- Enable Recommender API for idle IPs, disks, and VMs.
Note: Recommender insights can take time to appear and are not available for all services.
- Check for long-unused service accounts via logging:
(Put in code box) gcloud logging read 'resource.type="service_account"' --limit=50
Note: Look for accounts with no recent authentication or access events.
Cross-Cloud Tagging Strategy
Tagging isn't just for billing,it’s a security signal. Use these key tags:
- owner – Who created it
- purpose – Why it exists
- expiry – When it should be retired
- env – Dev, staging, prod
Best Practices
- Require tags at creation using policies (SCPs, Azure Policy, GCP Org Policy).
- Alert on untagged or stale resources.
- Use tags to scope scheduled cleanup jobs.
Alerting and Automation Logic
Scheduled Queries
- Run periodic queries against resource APIs or config logs.
- Filter for assets with no usage metrics or activity in 30+ days.
Cloud-Native Alerts
- AWS: CloudWatch alarms on low or zero usage metrics.
- Azure: Action Groups tied to Resource Graph alerts.
- GCP: Cloud Monitoring with alerting policies on idle states.
Scheduled Cleanup Workflows
- Use Lambda, Cloud Functions, or Azure Automation to:
- Log flagged ghost assets
- Notify resource owners
- Archive or delete after a grace period
Useful Tools for Multi-Cloud Cleanup
- Steampipe – Query multi-cloud resources with SQL.
- CloudQuery – Extract cloud data into a queryable database.
- Open Policy Agent (OPA) – Validate resource tags and policy compliance.
- Terraform + Terragrunt – Define lifecycle and expiration rules.
Sustaining Clean Cloud Environments
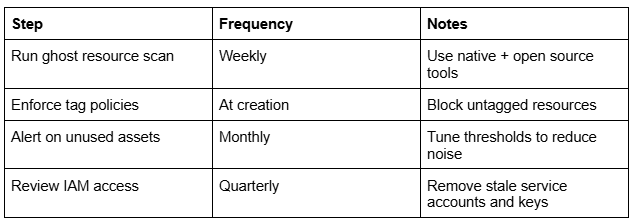
Conclusion
Zombie resources are silent risks. They inflate cloud bills and create soft targets for attackers. But with scheduled scans, tagging discipline, and simple automation, you can uncover and eliminate them before they become a problem.
Clean cloud environments don’t happen by accident. Build cleanup into your cloud operations like you do backups or monitoring, systematically and often.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand



