Securing Intercloud Identities: Mitigating Access Risks Across Providers

In today’s multi-cloud world, organisations are increasingly leveraging multiple cloud providers to maximise flexibility, cost efficiency, and scalability. While this approach offers significant advantages, it also introduces a few headaches, particularly when it comes to managing identities across different environments.
Think of it like trying to manage a security system where each door has a different lock, and the keys don’t always fit. Misconfigurations, inconsistent policies, and weak points around intercloud identities can be exploited if not carefully managed.
In this article, we’ll explore these challenges, uncover the risks, and offer practical ways to mitigate them.
The Challenge of Intercloud Identity Management
Imagine you’re juggling three different house keys for three different houses, each with its own set of rules for unlocking the door. This is essentially what managing identities across cloud providers like AWS, Azure, and Google Cloud Platform (GCP) feels like. Each platform has its own identity and access management (IAM) system, and trying to unify these without oversight can create security gaps.
For example, identity synchronisation might lead to over-permissive roles, much like giving someone access to not just the house but the garage, attic, and safe without intending to. If one cloud's identity
configuration is weaker than the others, attackers might find the weak spot and exploit it, gaining
access across multiple clouds.

Key Risks in Intercloud Identity Management
1. Cross-cloud Role Exploitation
Think of this like finding a spare key under a doormat. If identities are shared or synchronised across clouds and an attacker finds the weak point, they can "hop" from one cloud to another, exploiting over-permissive roles. They could easily move from cloud to cloud, increasing the potential damage.

2. Insufficient Monitoring and Logging:
It's like having security cameras but forgetting to turn half of them on. Without unified monitoring, attackers could move between clouds unnoticed. One cloud might detect suspicious activity, but if it’s not linked with the others, an intruder could slip through.
3. Credential Mismanagement:
Managing credentials in a multi-cloud setup can feel like trying to remember dozens of passwords for different accounts. Without the right strategy, misplaced credentials or mismanaged secrets can easily end up in the wrong hands.
4. Misconfigured Federated Access:
Federated access is like using a master key to access multiple doors. However, if the key is copied or misconfigured, it becomes a huge security risk. Attackers could use vulnerabilities in federated access to unlock doors across cloud environments, giving them broad, unintended access.
Best Practices for Securing Intercloud Identities
Here’s the good news: by following some key practices, you can ensure that your cloud identity
management doesn’t turn into an intercloud security nightmare. Let’s break it down:
1. Enforce Least Privilege Access Across Clouds
Imagine only giving each person the specific key to the room they need access to, and nothing more. That’s the idea behind least privilege access. By granting only the necessary permissions and regularly auditing roles, you reduce the risk of someone gaining access to the entire house when all they needed was the garage.
- Regularly review access and remove excess permissions.
- Use cloud tools like AWS IAM policies or Azure role-based access controls to keep access fine-tuned.
- Automate the monitoring of permissions and roles so you don’t need to manually check every key.
2. Implement Unified Identity Policies
Think of this like making sure every door in your multi-cloud house has the same lock system, so you know how each one works. Having unified policies across your cloud providers ensures consistency and reduces the chance of misconfigurations that leave some doors more vulnerable than others.
Cloud-native tools, such as AWS Identity Center and Azure AD, help unify these policies, so you can
manage everything in one place, like a central key ring.
3. Enhance Cross-cloud Visibility
It’s like upgrading from regular security cameras to a fully integrated system that watches all parts of the house at once. Centralised logging solutions like SIEM bring together logs from AWS, Azure, and GCP
into a single platform, giving you visibility across your entire multi-cloud environment.
This allows you to spot suspicious activity across different clouds in real time and take action before an attacker can move further.

4. Secure Federated Access Protocols
If federated access is the master key, you need to make sure it’s not duplicated or stolen. When using
protocols like SAML or OIDC, ensure they’re configured correctly and secured with Multi-factor Authentication (MFA) to add an extra layer of protection.
Regularly audit your federated connections to ensure everything is locked down. Misconfigured federations are like leaving the back door unlocked for someone to slip in unnoticed.

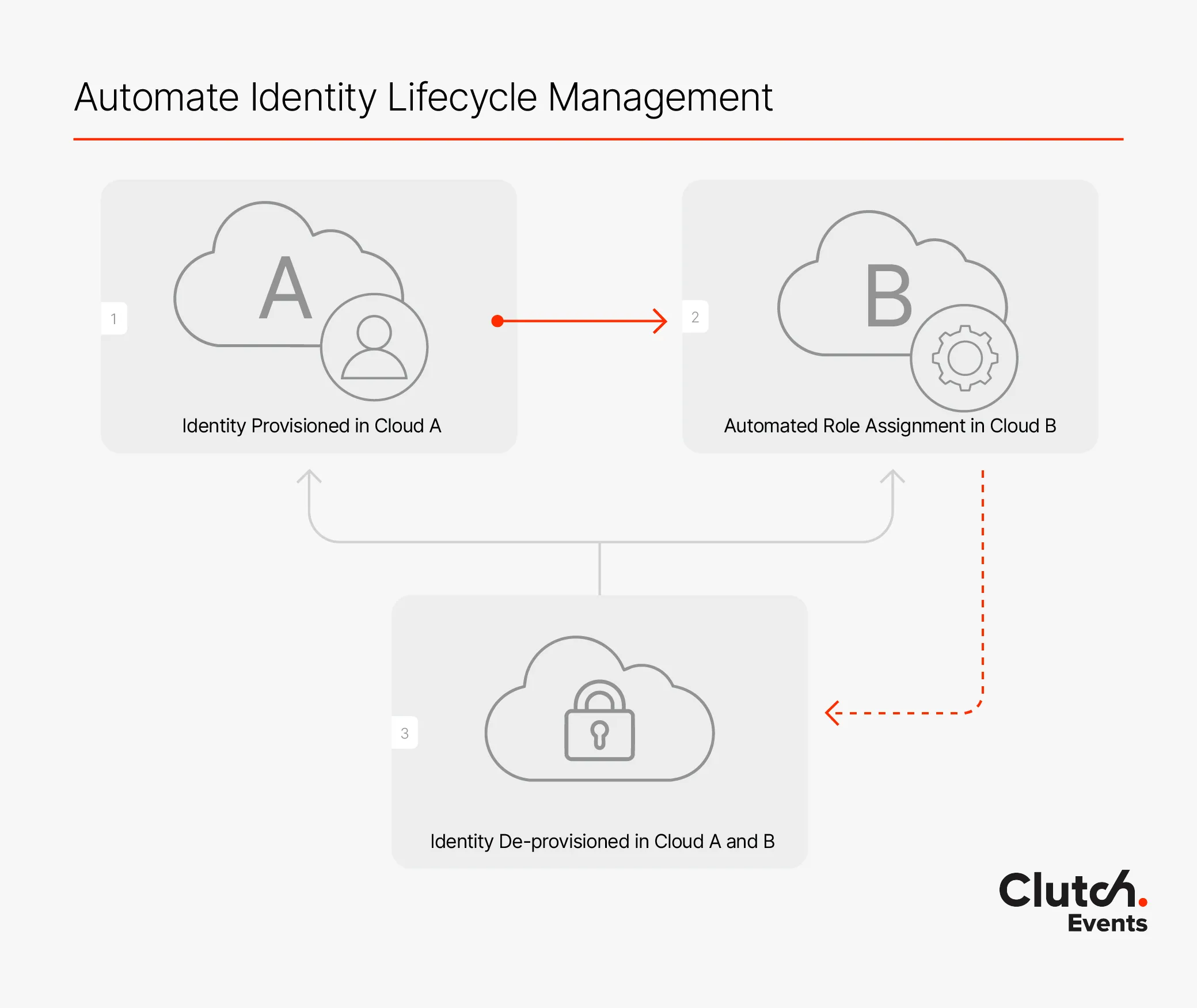
5. Automate Identity Lifecycle Management
Automation here is your best friend. Picture having a security system that automatically gives and takes away keys as people move in and out. By automating identity provisioning and de-provisioning across clouds, you reduce the risk of human error and ensure that nobody keeps keys longer than they should.
Tools like HashiCorp Vault or AWS Secrets Manager help automate the secure management of credentials, ensuring everything stays in sync without manual intervention.
Mitigating Threats to Intercloud Identities
Of course, attackers are always finding new ways to slip through the cracks, and intercloud identities are a tempting target. Credential stuffing, phishing, and man-in-the-middle attacks are like someone finding or stealing your house key, giving them access if you're not paying attention.
To stay ahead of these threats:
- Implement Zero Trust architectures that require continuous identity verification.
- Use Privileged Access Management (PAM) to ensure that sensitive identities are carefully guarded.
- Utilise behavioural analytics to monitor for unusual activity, like a key being used at odd
hours or in unexpected places.
Conclusion
Managing intercloud identities doesn’t have to feel like juggling too many keys. By following best practices
such as enforcing least privilege access, unifying identity policies, enhancing cross-cloud visibility, securing federated access, and automating lifecycle management, you can stay ahead of the risks.
In a multi-cloud world, identity management is your first line of defence. Securing it properly ensures that
your organisation can reap the benefits of cloud flexibility without leaving the doors wide open to attackers.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand



