When M&A Meets Cloud: Securing Multi-Tenant Environments During Post-Acquisition Chaos

Mergers and acquisitions often create sudden complexity in cloud environments. Teams must integrate infrastructure, identities, and applications fast. But without a plan, security gaps multiply.
This briefing explores how to secure multi-tenant cloud environments during M&A, and how to avoid the most common security failures when cloud estates collide.
Why M&A Creates Risk in the Cloud
1. Overlapping Accounts and Shadow Admins
- Acquired environments often include unmanaged IAM users, stale keys, and undocumented admin roles.
- There's little clarity on who has access to what and who should.
2. Conflicting Network Architectures
- VPC peering, overlapping CIDRs, and duplicate DNS zones complicate segmentation.
- Lift-and-shift integration often leads to flat networks with broad trust.
3. Inconsistent Security Control
- sOne org may use GuardDuty and WAF; the other doesn’t.
- Logging, alerting, and encryption standards vary or don’t exist.
4. Breakneck Timelines
- Security teams are often brought in late.
- The pressure to “connect the clouds” quickly leads to shortcuts.
What Security Leaders Must Do During Cloud Integration
1. Establish an Interim Access Model Immediately
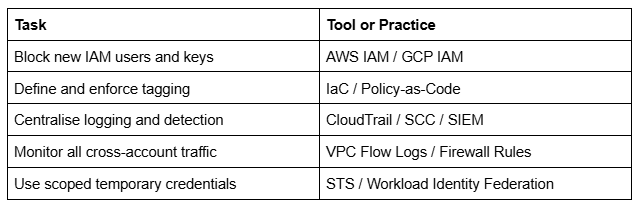
- Freeze new IAM users and keys until they’ve been reviewed.
- Require all integrations to use scoped, temporary credentials (e.g., AWS STS, GCP Workload Identity Federation).
- List all active role assumption paths using CloudTrail (AWS) or Audit Logs (GCP) to surface shadow access or undocumented trust relationships.
2. Map and Isolate Cloud Tenants
- Keep cloud accounts or projects separate until identities, network trust, and IAM strategy are defined.
- Use separate landing zones or folders in AWS Organizations / GCP Resource Manager.
- Build clear blast radius boundaries before initiating cross-cloud communication.
3. Define Integration Entry Points
- Create hardened APIs, message queues, or brokers for initial communication.
- Avoid full VPC-to-VPC trust unless segmenting with strict security groups or firewall rules.
- Monitor ingress and egress using shared observability tooling.
4. Normalize Security Baselines
- Apply minimum security standards: logging, encryption, tagging, and patching.
- Extend detection tooling (e.g., GuardDuty, Security Command Center*) to acquired environments.
- Use AWS Config or GCP SCC to identify deviations from baseline.
Note: GCP Security Command Center is not available on all GCP tiers. Verify project-level eligibility and enablement during onboarding.
5. Build a Joint Cloud Inventory
- Inventory all accounts, projects, regions, and environments involved.
- Map all IAM roles and service accounts across both environments.
- Track critical assets with consistent labels, tags, or resource naming conventions.
Often Overlooked: Shared quotas, org-level API limits, and billing account overlaps across merged clouds can delay provisioning or impact availability. Include quota, org, and billing architecture in your integration risk assessment.
Long-Term Strategy: Build for Secure Multi-Tenancy
- Move to account-per-team or project-per-app structure.
- Use org-wide policies (SCPs in AWS, Organization Policies in GCP) to enforce baseline standards.
- Delegate access using federated identity providers, not static IAM users.
- Monitor with a unified control plane (e.g., SIEM, CSPM), not siloed cloud consoles.
Post-M&A Security Checklist
Final Thoughts
M&A chaos is normal but letting security slip isn’t. The first 90 days after an acquisition shape your long-term cloud risk posture.
Treat integration as a controlled, multi-tenant operation, not a lift-and-merge. Build boundaries first. Bridge them carefully.
Speed will always be expected. Security has to be deliberate.
Related Resources
Find your Tribe
Membership is by approval only. We'll review your LinkedIn to make sure the Tribe stays community focused, relevant and genuinely useful.
To join, you’ll need to meet these criteria:
> You are not a vendor, consultant, recruiter or salesperson
> You’re a practitioner inside a business (no consultancies)
> You’re based in Australia or New Zealand



